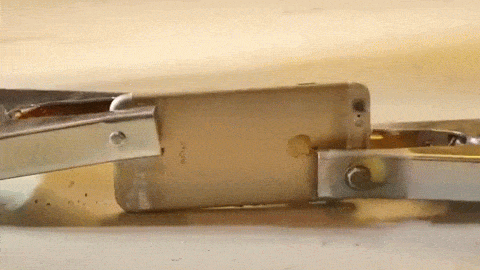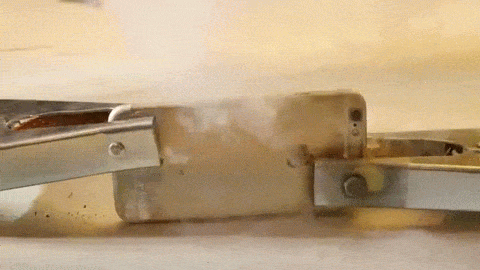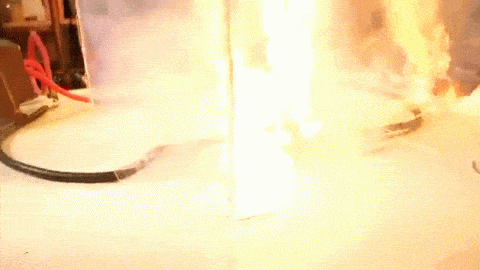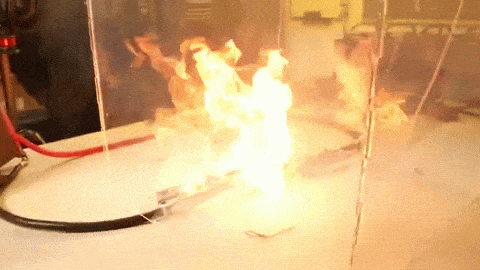
On December 2, 2015, [Syed Rizwan Farook] and [Tashfeen Malik] opened fire at a San Bernardino County Department of Public Health training event, killing 14 and injuring 22. This was the third deadliest mass shooting in the United States in recent memory, and began a large investigation by local, state, and federal agencies. One piece of evidence recovered by the FBI was an iPhone 5C belonging to one of the shooters. In the days and months after the shooting, the FBI turned to Apple to extract data from this phone.
A few days ago in an open letter to customers, [Tim Cook], CEO of Apple, stated they will not comply with FBI’s request to build a backdoor for the iPhone. While the issue at hand is extracting data from an iPhone recovered from the San Bernardino shooting, [Cook] says building a new version of iOS to extract this data would allow the FBI to unlock any iPhone. Needless to say, there are obvious security implications of this request.
Apple does not publish open letters to its customers often. Having one of the largest companies on the planet come out in support of privacy and encryption is nearly unprecedented. There is well-founded speculation this open letter to the public will be exhibit A in a supreme court case. Needless to say, the Internet has gone a little crazy after this letter was published, and rightly so: just imagine how better off we would be if AT&T said no to the NSA in 2002 – [Snowden] might just be another IT geek working for a government contractor.
 There is a peculiar aspect of public discourse that doesn’t make any sense. In the absence of being able to say anything interesting, some people have just decided to add a contrary viewpoint. Being right, having a valid argument, or even having evidence to support assertions doesn’t matter; being contrary is far more interesting. Look at any comment thread on the Internet, and you’ll find the longest comment chain is the one refuting the parent article. Look up the ratings for a cable news channel. You’ll find the highest rated show is the one with the most bickering. When is the last time you saw something from the New York Times, Washington Post, or LA Times on Facebook or your favorite news aggregator? Chances are, it wasn’t news. It was an op-ed, most likely one that was espousing a view contrary to either public opinion or public policy.
There is a peculiar aspect of public discourse that doesn’t make any sense. In the absence of being able to say anything interesting, some people have just decided to add a contrary viewpoint. Being right, having a valid argument, or even having evidence to support assertions doesn’t matter; being contrary is far more interesting. Look at any comment thread on the Internet, and you’ll find the longest comment chain is the one refuting the parent article. Look up the ratings for a cable news channel. You’ll find the highest rated show is the one with the most bickering. When is the last time you saw something from the New York Times, Washington Post, or LA Times on Facebook or your favorite news aggregator? Chances are, it wasn’t news. It was an op-ed, most likely one that was espousing a view contrary to either public opinion or public policy.
As with any headline event on the Internet, the contrarians have come out of the woodwork. These contrarians are technically correct and exceedingly myopic.
Continue reading “The Contrarian Response To Apple’s Need For Encryption” →



 There is a peculiar aspect of public discourse that doesn’t make any sense. In the absence of being able to say anything interesting, some people have just decided to add a contrary viewpoint. Being right, having a valid argument, or even having evidence to support assertions doesn’t matter; being contrary is far more interesting. Look at any comment thread on the Internet, and you’ll find the longest comment chain is the one refuting the parent article. Look up the ratings for a cable news channel. You’ll find the highest rated show is the one with the most bickering. When is the last time you saw something from the New York Times, Washington Post, or LA Times on Facebook or your favorite news aggregator? Chances are, it wasn’t news. It was an op-ed, most likely one that was espousing a view contrary to either public opinion or public policy.
There is a peculiar aspect of public discourse that doesn’t make any sense. In the absence of being able to say anything interesting, some people have just decided to add a contrary viewpoint. Being right, having a valid argument, or even having evidence to support assertions doesn’t matter; being contrary is far more interesting. Look at any comment thread on the Internet, and you’ll find the longest comment chain is the one refuting the parent article. Look up the ratings for a cable news channel. You’ll find the highest rated show is the one with the most bickering. When is the last time you saw something from the New York Times, Washington Post, or LA Times on Facebook or your favorite news aggregator? Chances are, it wasn’t news. It was an op-ed, most likely one that was espousing a view contrary to either public opinion or public policy.