We’ve seen a lot of PCIe hacks on Hackaday, and a fair few of them boil down to hackers pulling PCIe somewhere it wasn’t meant to be. Today, we routinely can find PCIe x1, x2 and x4 links sitting around in our tech, thanks to the proliferation of things like NVMe SSDs, and powerful cheap SoCs that make PCIe appear at your fingertips.
In the PCIe For Hackers series, we’ve talked about PCIe and how cool it is, all the benefits it has for hackers, gave you layout and interconnection rules, and even went into things like PCIe switches and bifurcation. However, there’s one topic we didn’t touch much upon, and that’s external PCIe links.
Today, I’d like to tell you about OCuLink – a standard that hackers might not yet know as an option whenever we need to pull PCIe outside of your project box, currently becoming all that more popular in eGPU space. Essentially, OCuLink is to PCIe is what eSATA is to SATA, and if you want to do an eGPU or an external “PCIe socket”, OCuLink could work wonders for you.
Respectable Capabilities
Just like any high-speed standard, PCIe has some tight requirements when things get fast. Even though PCIe is known to be not as sensitive to lower-quality links due to its link training and generation downgrade abilities, at higher link speeds, even through-hole vs SMD sockets can make a difference. So, if you want to go high-throughput, you want proper cabling and connectors, intended for out-of-chassis use – and OCuLink gives you all of this, at a low price.
Continue reading “PCIe For Hackers: External PCIe And OCuLink”


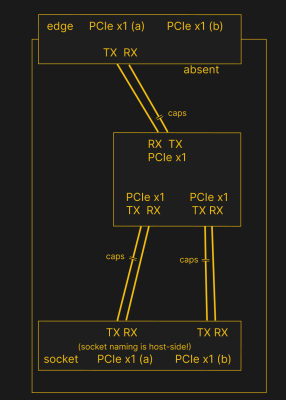 PCIe needs TX pairs connected to RX on another end, like UART – and this is non-negotiable. Connectors will use host-side naming, and vice-versa. As the diagram demonstrates, we connect the socket’s TX to chip’s RX and vice-versa; if we ever get confused, the laptop schematic is there to help us make things clear. To sum up, we only need to flip the names on the link coming to the PCIe switch, since the PCIe switch acts as a device on the card; the two links from the switch go to the E-key socket, and for that socket’s purposes, the PCIe switch acts as a host.
PCIe needs TX pairs connected to RX on another end, like UART – and this is non-negotiable. Connectors will use host-side naming, and vice-versa. As the diagram demonstrates, we connect the socket’s TX to chip’s RX and vice-versa; if we ever get confused, the laptop schematic is there to help us make things clear. To sum up, we only need to flip the names on the link coming to the PCIe switch, since the PCIe switch acts as a device on the card; the two links from the switch go to the E-key socket, and for that socket’s purposes, the PCIe switch acts as a host.
 You might have heard the term “bifurcation” if you’ve been around PCIe, especially in mining or PC tinkering communities. This is splitting a PCIe slot into multiple PCIe links, and as you can imagine, it’s quite tasty of a feature for hackers; you don’t need any extra hardware, really, all you need is to add a buffer for REFCLK. See, it’s still needed by every single extra port you get – but you can’t physically just pull the same clock diffpair to all the slots at once, since that will result in stubs and, consequently, signal reflections; a REFCLK buffer chip takes the clock from the host and produces a number of identical copies of the REFCLK signal that you then pull standalone. You might have seen x16 to four NVMe slot cards online – invariably, somewhere in the corner of the card, you can spot the REFCLK buffer chip. In a perfect scenario, this is all you need to get more PCIe out of your PCIe.
You might have heard the term “bifurcation” if you’ve been around PCIe, especially in mining or PC tinkering communities. This is splitting a PCIe slot into multiple PCIe links, and as you can imagine, it’s quite tasty of a feature for hackers; you don’t need any extra hardware, really, all you need is to add a buffer for REFCLK. See, it’s still needed by every single extra port you get – but you can’t physically just pull the same clock diffpair to all the slots at once, since that will result in stubs and, consequently, signal reflections; a REFCLK buffer chip takes the clock from the host and produces a number of identical copies of the REFCLK signal that you then pull standalone. You might have seen x16 to four NVMe slot cards online – invariably, somewhere in the corner of the card, you can spot the REFCLK buffer chip. In a perfect scenario, this is all you need to get more PCIe out of your PCIe.








