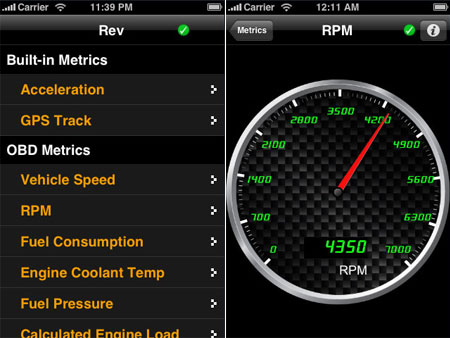
Rev by DevToaster is an application for the iPhone and iPod Touch that allows real-time monitoring of vehicle ECU data from the OBD-II port. Rev interfaces with a WiFi OBD-II dongle.
If your check engine light is on or flashing, REV is able to check the engine code, list all of the engine codes stored in the vehicle, and reset the stored codes or check engine light.
Rev is able to monitor real-time; vehicle speed, RPM, fuel consumption, engine coolant temp, fuel pressure, calculated engine load, throttle position, intake manifold pressure, air intake temp, timing advance, mass air flow, fuel level, barometric pressure, EVAP system vapor pressure, and fuel trim.
A brief video of REV in action is after the break.