[Johannes 4GNU_Linux] has been filming a video series on how to write Linux device drivers for a couple of years now, but luckily, you won’t need that long to watch them or to create your own driver. He’s added some recent videos to the series, like the one below, but might want to rewind a few years and start at the beginning.
If you build your own hardware for Linux, you’ll probably eventually want to write a driver which runs as a privileged program. While there are many things you can do in user space, for the ultimate control and performance, you can’t beat a driver.
One problem, though, is that drivers can really crash your system in a big way. In the old days, it was common to have a dedicated system for driver development. Today, for many drivers, you can get away with running a virtual machine that you can crash and reload without much trouble.
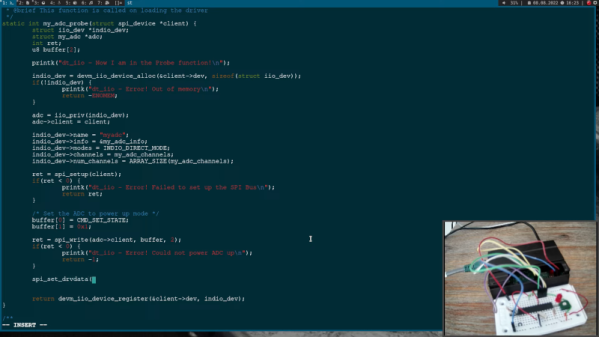
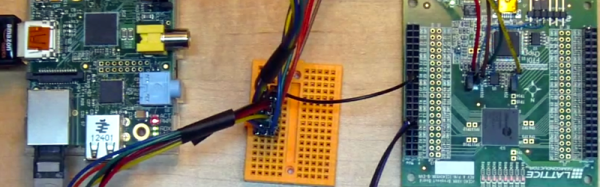
The videos cover diverse topics like interrupts, completions, polling, and threads. He even uses a Raspberry Pi, which will be very useful for many embedded projects. Of course, the trend these days is to have one driver — like the USB driver — and have it provide user-space access so that everyone doesn’t have to write their own drivers. But, as usual, that only goes so far.
We aren’t sure how many more videos there will be, but if you make it through the first 31, maybe more will be waiting for you. It has been a while since we looked at SPI drivers in Linux. As an example of why you might want to roll your own, consider a custom FPGA driver.