Many users of YouTube feel that the quality of the service has been decreasing in recent years — the platform offers up bizarre recommendations, fails to provide relevant search results, and continues to shove an increasing amount of ads into the videos themselves. For shareholders of Google’s parent company, though, this is a feature and not a bug; and since shareholder opinion is valued much more highly than user opinion, the user experience will likely continue to decline. But if you’re willing to put a bit of effort in you can stop a large chunk of YouTube ads from making it to your own computers and smartphones.
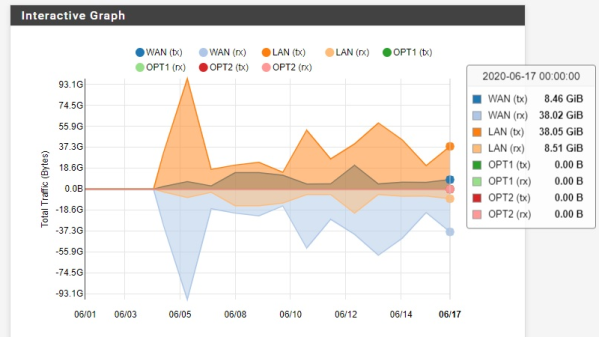
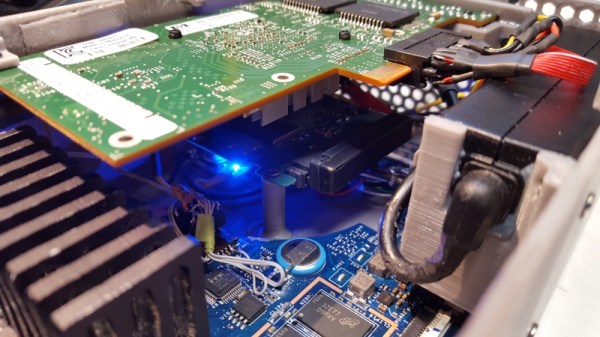
[Eric] is setting up this adblocking system on his entire network, so running something like Pi-hole on a single-board computer wouldn’t have the performance needed. Instead, he’s installing the pfSense router software on a mini PC. To start, [Eric] sets up a pretty effective generic adblocker in pfSense to replace his Pi-hole, which does an excellent job, but YouTube is a different beast when it comes to serving ads especially on Android and iOS apps. One initial attempt to at least reduce ads was to subtly send YouTube traffic through a VPN to a country with fewer ads, in this case Italy, but this solution didn’t pan out long-term.
A few other false starts later, all of which are documented in detail by [Eric] for those following along, and eventually he settled on a solution which is effectively a man-in-the-middle attack between any device on his network and the Google ad servers. His router is still not powerful enough to decode this information on the fly but his trick to get around that is to effectively corrupt the incoming advertising data with a few bad bytes so they aren’t able to be displayed on any devices on the network. It’s an effective and unique solution, and one that Google hopefully won’t be able to patch anytime soon. There are some other ways to improve the miserable stock YouTube experience that we have seen as well, like bringing back the dislike button.
Thanks to [Jack] for the tip!