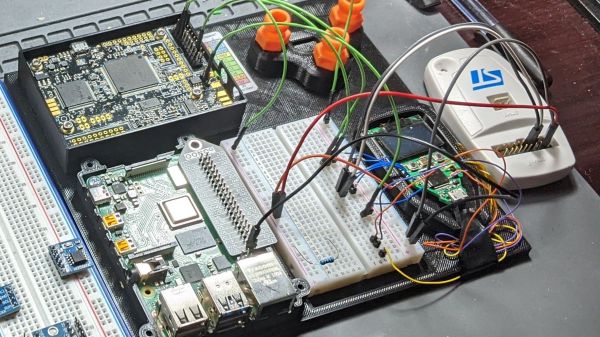
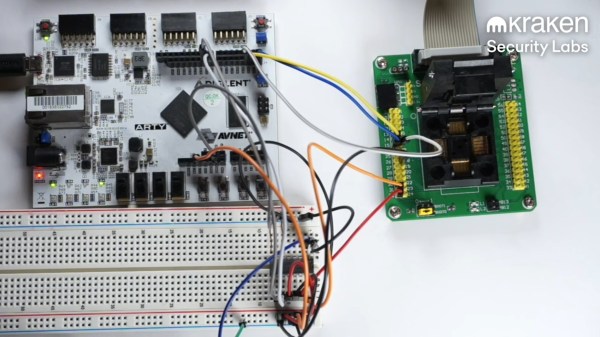
If you’ve always been intrigued by the idea of performing hardware attacks but never knew where to start, then we’ve got the article for you: an in-depth look at the hows and whys of hardware glitching.
Attentive readers will recall that we’ve featured [Matthew Alt]’s reverse engineering exploits before, like the time he got root on a Linux-based arcade cabinet. For something a bit more challenging, he chose a Trezor One crypto wallet this time. We briefly covered a high-stakes hack (third item) on one of these wallets by [Joe Grand] a while back, but [Matthew] offers much, much more detail.
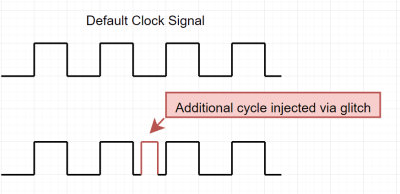 After introducing the theory of glitching attacks, which seek to force a processor into an undefined state using various methods, [Matthew] discusses the specifics of the Trezor wallet and how the attack was planned.
After introducing the theory of glitching attacks, which seek to force a processor into an undefined state using various methods, [Matthew] discusses the specifics of the Trezor wallet and how the attack was planned.
His target — the internal voltage regulator of the wallet’s STM32 microcontroller — required desoldering a few caps before the attack could begin, which was performed with a ChipWhisperer. After resolving a few initial timing issues, he was able to glitch the chip into dropping to the lowest level of readout protection, which gave access to the dongle’s SRAM through an ST-Link debugger.
While this summary may make the whole thing sound trivial, it’s obvious that the attack was anything but, nor was the effort that went into writing it all up. The whole thing reads a little like a techno-thriller, and there’s plenty of detail there if you’re looking for a tutorial on chip glitching. We’re looking forward to part 2, which will concentrate on electromagnetic fault-injection using a PicoEMP and what looks like a modified 3D printer.