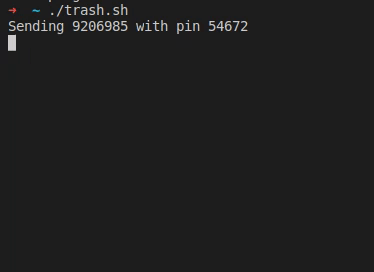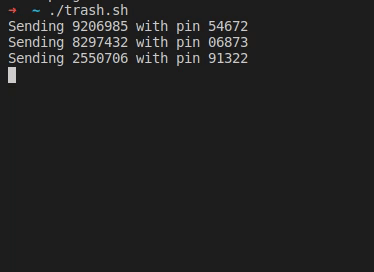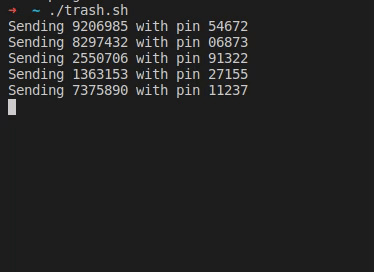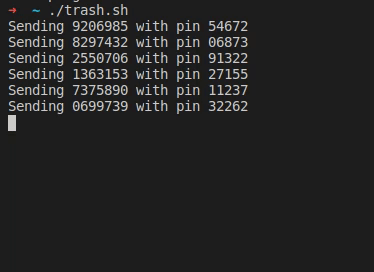
There’s a new SSH vulnerability, Terrapin (pdf paper), and it’s got the potential to be nasty — but only in an extremely limited circumstance. To understand the problem, we have to understand what SSH is designed to do. It replaces telnet as a tool to get a command line shell on a remote computer. Telnet send all that text in the clear, but SSH wraps it all inside a public-key encrypted tunnel. It was designed to safely negotiate an unfriendly network, which is why SSH clients are so explicit about accepting new keys, and alerting when a key has changed.
SSH uses a sequence counter to detect Man-in-the-Middle (MitM) shenanigans like packet deletion, replay, or reordering. That sequence isn’t actually included in the packet, but is used as part of the Message Authentication Check (MAC) of several encryption modes. This means that if a packet is removed from the encrypted tunnel, the MAC fails on the rest of the packets, triggering a complete connection reset. This sequence actually starts at zero, with the first unencrypted packet sent after the version banners are exchanged. In theory, this means that an attacker fiddling with packets in the pre-encryption phase will invalidate the entire connection as well. There’s just one problem.
The innovation from the Terrapin researchers is that an attacker with MitM access to the connection can insert a number of benign messages in the pre-encryption phase, and then silently drop the first number of messages in the encrypted phase. Just a little TCP sequence rewriting for any messages between, and neither the server nor client can detect the deception. It’s a really interesting trick — but what can we do with it?
For most SSH implementations, not much. The 9.6 release of OpenSSH addresses the bug, calling it cryptographically novel, but noting that the actual impact is limited to disabling some of the timing obfuscation features added to release 9.5.
Continue reading “This Week In Security: Terrapin, Seized Unseized, And Autospill”