Most people don’t think too much of vending machines. They’re just those hulking machines that lurk around on train stations, airports and in the bowels of school and office buildings, where you can exchange far too much money for a drink or a snack. What few people are aware of is just how these vending machines have changed over the decades, to the point where they’re now collecting any shred of information on who interacts with them, down to their age and gender.
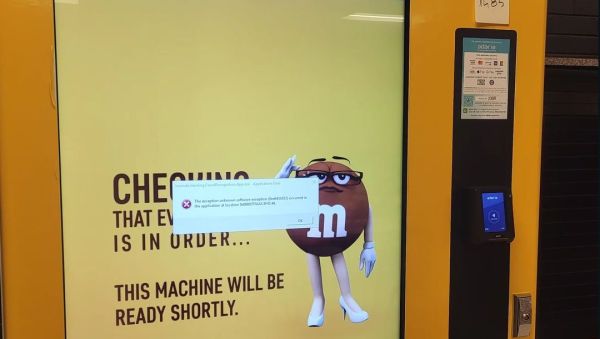
How do we know this? We have a few enterprising students at the University of Waterloo to thank. After [SquidKid47] posted a troubling error message displayed by a campus M&M vending machine on Reddit, [River Stanley] decided to investigate the situation. The resulting article was published in the February 16th edition of the university’s digital newspaper, mathNEWS.
In a bout of what the publication refers to as “Actual Journalism”, [Stanley] found that the machine in question was produced by Invenda, who in their brochure (PDF) excitedly note the many ways in which statistics like age, gender, foot traffic, session time and product demographics can be collected. This data, which includes the feed from an always-on camera, is then processed and ‘anonymized statistics’ are sent to central servers for perusal by the vending machine owner.
The good news is that this probably doesn’t mean that facial recognition and similar personalized information is stored (or sent to the big vaporous mainframe) as this would violate the GDPR and similar data privacy laws, but there is precedence of information kiosks at a mall operator taking more liberties. Although the University of Waterloo has said that these particular vending machines will be removed, there’s something uncomfortable about knowing that those previously benign vending machines are now increasingly more like the telescreens in Orwell’s Nineteen Eighty-Four. Perhaps we’re already at the point in this timeline were it’s best to assume that even vending machines are always watching and listening, to learn our most intimate snacking and drinking habits.
Thanks to [Albert Hall] for the tip.