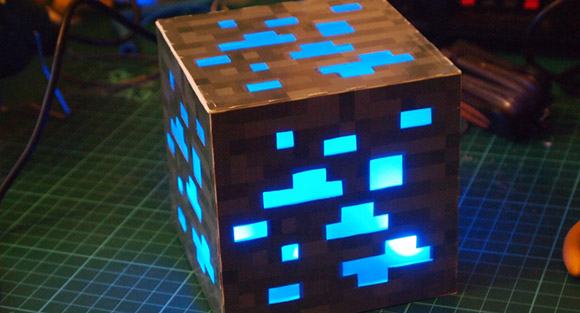
[Ryan] has a friend with a birthday coming up, and being inspired by ever 12-year-olds favorite game, he decided to make a Minecraft ore block with RGB LEDs. The block can change from diamonds to emeralds via commands send from an Android phone.
After a few false starts, [Ryan] eventually had his ore cube laser cut at Acess Space, a hackerspace-ish group in Sheffield. The box was constructed out of 3mm MDF, while the windows were laser cut out of frosted acrylic, while the stone pattern on the cube is one giant custom-made sticker.
With the tedious part of the build out of the way, [Ryan] set to work on the electronics. He used a PIC attached to a few very large RGB LEDs, and a Bluetooth module that allows him to connect his phone to an ore block. Dialing in the right colors took some work, but eventually, [Ryan] had an Android-controlled Minecraft ore block, able to transmutate between gold, iron, diamond, emerald, lapis, and redstone.
You can check out a video of [Ryan]’s ore block in action after the break.