The folks at Matasano Security and Square have teamed up to build an online capture the flag (CTF) competition. The Microcorruption CTF focuses on embedded security and challenges players to reverse engineer a fictional “Lockitall LockIT Pro” lock system.
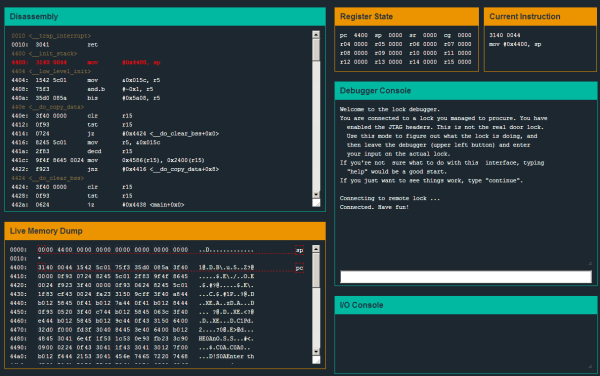
Each level places you in a debugging environment with a disassembly listing, live memory view, register view, and debugging console. You can set breakpoints, step through code, and modify registers like in a real debugging environment. Your goal is to figure out how to bypass the lock to collect bearer bonds.
While the device and motive may be fictional, the assembly is actual MSP430 code. The debugger is similar to GDB connected to a remote target using OpenOCD. There’s even a manual (PDF) to help you get up to speed with writing MSP430 code for the device.
This CTF looks like a great introduction to embedded security, and doesn’t require buying real hardware. It even includes a full tutorial to get you started.