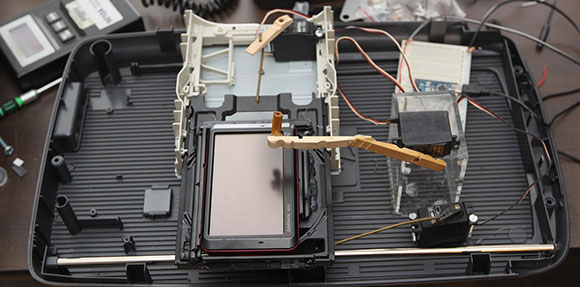
[JJ] picked up a Garmin Nuvi 780 GPS from an auction recently. One of the more frustrating features [JJ] ran into is it’s PIN code; this GPS can’t be unlocked unless a four-digit code is entered, or it’s taken to a ‘safe location’. Not wanting to let his auction windfall go to waste, [JJ] rigged up an automated brute force cracking robot to unlock this GPS.
The robot is built around an old HP scanner and a DVD drive sled to move the GPS in the X and Y axes. A clever little device made out of an eraser tip and a servo taps out every code from 0000 to 9999 and waits a bit to see if the device unlocks. It takes around 8 seconds for [JJ]’s robot to enter a single code, so entering all 10,000 PINs will take about a day and a half.
Fortunately, the people who enter these codes don’t care too much about the security of their GPS devices. The code used to unlock [JJ]’s GPS was 0248. It only took a couple of hours for the robot to enter the right code; we’d call that time well spent.
You can check out the brute force robot in action after the break.















