Free-formed VFD clock
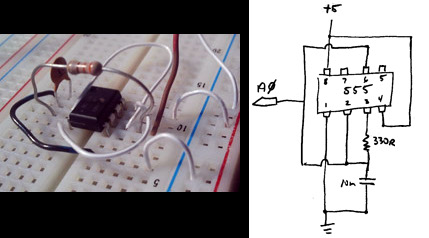
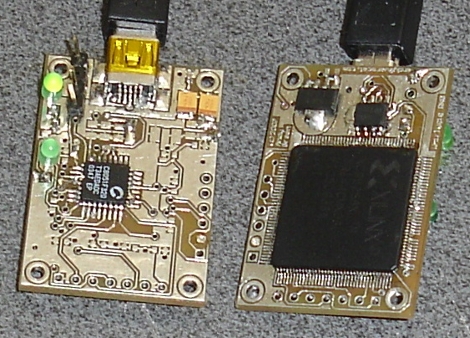
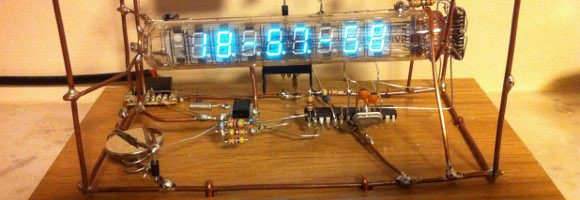 [James] doesn’t need a circuit board or even some protoboard to get the job done. He free-formed all the circuits for his VFD clock. Right now this is the only project hosted on his blog so click around to see how he got to this point.
[James] doesn’t need a circuit board or even some protoboard to get the job done. He free-formed all the circuits for his VFD clock. Right now this is the only project hosted on his blog so click around to see how he got to this point.
DIY LED traffic light
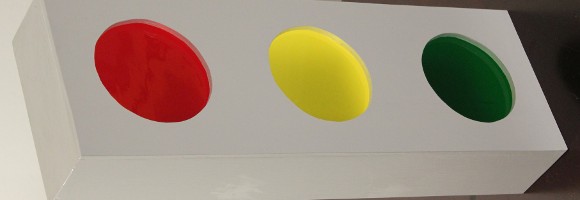
Here’s a scratch-build traffic light which [Jarle] uses to display information about his server. If you’re unable to find your own storm damaged original this is a pretty easy way to build one.
FPGA space attack game

This game is running on an FPGA, but it’s not written in HDL. Instead, [Johan] wrote the game in C to run on a soft processor loaded on the gate array.
Hourglass entropy

This is a fascinating idea for generating random numbers. [Gijs] is shining a laser onto a light dependent transistor. The beam of the laser is broken by the falling sand of an hourglass. This technique could be use as an entropy source for random number generation.
GPS clock source for a digital timepiece
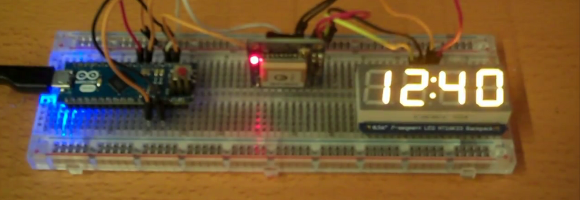
It seems like massive overkill, but you can’t beat the time accuracy of using a GPS module as a clock source. We don’t expect that [Jay] kept the clock in one piece after finishing the project. It’s just a good way to practice decoding the GPS data.