[Fileark] has instructions for reprogramming keyless entry devices for your car. His demonstration video, which you can see after the break, shows how to make one key fob work for two different vehicles. In this case he’s working on a couple of Chevrolet trucks but there are instructions for GM, Ford, Dodge, Toyota, and Nissan. If you need to reprogram one of these you may find this useful, but we’re wondering how it can be incorporated into a project. If you can sniff out the communications that are going on during the programming you should be able to build and pair your own devices with a vehicle. Wouldn’t it be nice to incorporate your keyless entry into your wristwatch?
key38 Articles
RGB Keylock Shield

Hackaday alum [Will O’Brien] cleaned up his messy breadboard with an RGB keylock Arduino shield. You may remember this two-part project from last year. It uses buttons backlit by an RGB LED to operate a door lock.
[Will] is still mulling over what type of kit options he will offer. We’re happy to see if the most important part, a laser-cut key bezel, will be available. This makes for a professional looking finish that made the original project difficult to replicate.
Two-factor Authentication Using A Hardware Token

We ran into a friend a while back who was logging into her employer’s Virtual Private Network on the weekend. She caught our attention by whipping out her keys and typing in some information from a key-fob. It turns out that her work uses an additional layer of protection for logging into the network. They have implemented a username, pin number, as well as a hardware token system called SecurID.
The hardware consists of a key-fob with an LCD screen on it. A code is displayed on the screen and changes frequently, usually every 60 seconds. The device is generating keys based on a 128-bit encryption seed. When this number is fed to a server that has a copy of that seed, it is used as an additional verification to the other login data.
This seems like a tech trickle-down of the code generating device from GoldenEye. It does get us thinking: with the problems free email services have been having with account theft, why aren’t they offering a fee-based service that includes a security fob? With the right pricing structure this could be a nice stream of income for the provider. We’re also wondering if this can be implemented with a microcontroller and used in our home network. As always, leave comments below and let us know if you’ve already built your own system using these principles.
Update: Thanks to Andre for his comment that tells us this type of security is available for Apache servers. The distribution includes a server side authentication system and a Java based token generator that can run on any handheld that supports Java.
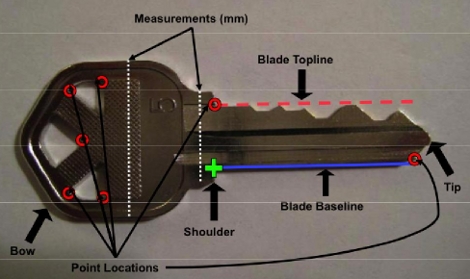
Photographic Key Duplication
[Ben] and his associates over at the University of California at San Diego came up with a way to duplicate keys using a picture of them. They developed an algorithm that uses measurements from known key blanks to extrapolate the bitting code. Because the software is measuring multiple points it can correct the perspective of the photo when the key is not photographed on a flat surface, but from an angle.
They went so far as to test with cell phone cameras and using a telephoto lens from 195 feet away. In most cases, correct keys were produced within four guesses. Don’t miss their wonderful writeup (PDF) detailing how key bitting works, traditional covert duplication methods, and all the details of their process. The lack of available code prevents us all from playing secret agent (or felon) with this idea but [Ben] did mention that if there is sufficient interest he might release it.
Lock bumping showed us how weak our security is, but this is a bit scary.
[Thanks Mike]
Impressioning At LockCon

[Steffen Wernéry] has published a video of the impressioning contest at LockCon. We learned about key impressioning at this year’s HOPE conference. You start the process by inserting a key blank into the lock. By turning the lock until it stops and then moving the key up and down you create marks on the blank’s face. Take a file to those marks to remove the extra material and then repeat the process. Once the pins are set properly, they’ll stop leaving marks on the blank. It takes a lot of skill to do this right, but you end up with a perfectly functional key. [Barry Wels] managed to win the competition in 5:30 with second place coming in at 6 minutes.
LockCon Coming Soon

The Open Organisation Of Lockpickers (TOOOL) is planning a new annual gathering for lockpickers. October 9-12th they will hold the first ever LockCon in Sneek, Netherlands. The event was spawned from the Dutch Open lockpicking championships, but they’ve decided to expand beyond just competition into a full conference. This year the conference is limited to just 100 lockpickers, technicians, manufacturers, hackers, and law enforcement members. They’ll compete in picking competitions, safe manipulation, and key impressioning.
On a related note: Organizer [Barry Wels] just became the first non-German to win an SSDeV competition with his key impressioning skills. We covered key impressioning when we saw his talk about high security keys at The Last Hope. He says it’s only been about two years worth of study and 500 keys to become a master. He managed to open the lock in 5:13 filing two whole keys during that time.
[photo: Rija 2.0]
Red Hat Confirms Security Breach

After a week of wondering, Red Hat has confirmed that someone broke in and compromised their security. Although It doesn’t appear the attacker was able to retrieve the passphrase used to sign Fedora packages, the team is switching to new keys. In a separate intrusion the attacker tampered with and signed OpenSSH packages for RHEL. While it’s good to get the full story, no one is happy how long it took Red Hat to release these details.
[via Zero Day]
[photo: afsilva]