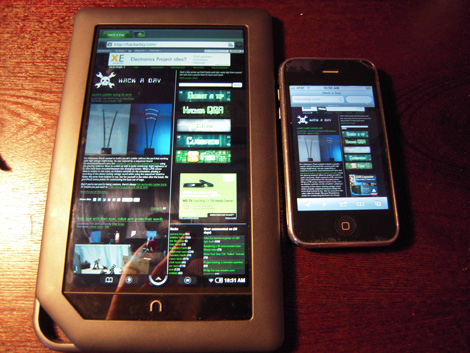
[Deeper-blue] has released all the files necessary to get Android honeycomb working on your nook color. We had a chance to play with the nook color for a bit, but ours was only on Android version 2.1. It seems like they’ve come a long way with the capabilities of this simple e-reader since then. While he’s built out the majority of the features, it is still lacking some fundamentals, like sound. As you can see in the video after the break, the scrolling is a tiny bit choppy but the applications themselves see to be fairly snappy. We can’t wait to see how this works after a little improvement.