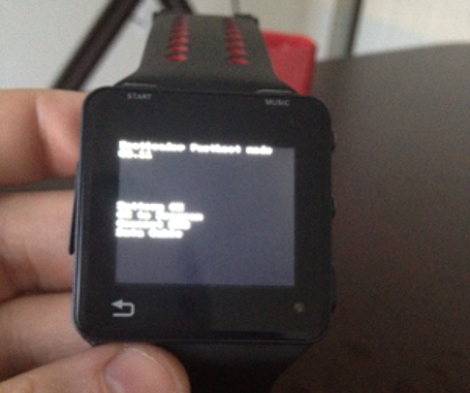
[Chris’] family made the mistake of giving him a hackable Christmas gift. We’d bet they didn’t see much of him for the rest of the day as he set about rooting this Android wristwatch.
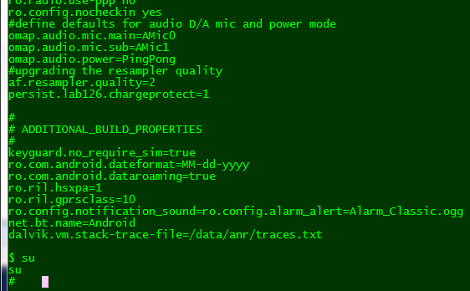
This thing has some pretty powerful hardware under the hood. It’s sporting an OMAP3 processor running at 600 MHz along with 256 MB of RAM. [Chris] needed to get his hands on a firmware image in order to look for security holes. He found a way to spoof the update application in order to intercept an upgrade image from the Internet.
He dumped the firmware locations and got to work searching for a way to exploit the device. Details are a bit scarce about want exactly he did, but you can download his modified image, letting you root your own Motorola Actv using the Android Debug Bridge.
We’ve embedded a demo video after the break. The OS is pretty snappy on the tiny device. We’re not sure what will come of this functionality, but we assume [Chris] was really only interested in the challenge of rooting process itself.
Continue reading “Rooting A Motorola Actv (Android Wristwatch)”