
[GlacialWanderer] has published the first pictures from his CNC machine build. It’s a three axis gantry style machine that he intends to route and engrave wood with. He’s posted a detailed cost breakdown: $1800. He estimates spending 30 hours researching on sites like CNCzone. The build time for the mechanical side was around 50 hours. The electrical system hasn’t been hoooked up yet, so look for that in a future post. It looks like an incredible machine already, so we can’t wait to see what’s next.
router197 Articles
Netgear Open Source Router

Netgear recently launched the WGR614L wireless router targeted specifically at open source firmware enthusiasts. It can use Tomato, DD-WRT, and soon OpenWRT. The core is a 240MHz MIPS processor with 16MB of flash and 4MB of RAM. You’ll probably remember when Linksys decided to dump Linux from their iconic WRT54G line in favor of VxWorks; they released the similarly speced WRT54GL for enthusiasts. Netgear seems to be arriving pretty late in the game, but they’ve set up a community specifically for this router. Time will tell whether community support is enough to make this the router of choice for hackers. We wish someone would release an x86 based router in the same price range just to make porting stupidly simple.
[via Slashdot]
In Car WiFi

You may have already heard that Chrysler is planning to provide in-car wireless internet access to its vehicles. If not, expect to hear more about it later this year when the requisite hardware becomes a sales-floor option, or next year when it becomes factory standard for some cars.
We can’t say it’s a bad idea, it’s just not a new one. Plenty of commercial portable routers are available, but they still need a modem and data plan to provide internet access. For internet access and wireless routing, look to [Nate True]’s cellphone-router combo, which uses a spare Nokia cellphone and a highly modded Wi-Fi router running OpenWRT. [True] has made it easy by providing the instructions and necessary custom code, but it seems like a lot of effort for a relatively slow connection. We think the original Stompbox is still the most fun since it has the speed of commercial devices and an open x86 OS to modify.
Malware Alters DNS Data On Routers

The Zlob trojan, also known as DNSChanger, has been around for a few years, but recent Zlob variants to appear in the wild attempt to log into routers using a list of default admin/password combos. If they succeed, they alter the DNS records on the router to reroute traffic through the attacker’s server.
Our friend [Dan Kaminisky] recently did a presentation warning against vulnerabilities in internet browser plugins that allow attackers to mount DNS rebinding attacks against routers with default passwords.. Though it achieves the same end, Zlob is different because it infects by the tried-and-true method of fooling users into downloading it inside a fake video codec. Once it is running on a client machine, it is free to attempt to use the default admin id and password of the router to log in and alter DNS settings. It even supports the DD-WRT firmware.
Even if a system is wiped clean of Zlob trojans, the router could still be compromised. The good news is that it is easy to fix and even easier to prevent. Fixing it takes no more than wiping all network clients clean, then resetting the router and restoring custom settings. Prevention is a simple matter of changing the router’s password.
[photo: fbz]
DNS Spoofing With Ettercap

[IronGeek] has published his latest video how-to: DNS Spoofing with Ettercap. Ettercap is designed specifically to perform man in the middle attacks on your local network. It can do ARP poisoning, collect passwords, fingerprint OSes, and content filtering. For DNS spoofing, you just need to edit a config file that defines which domains resolve to which IP addresses. You can use wildcards for the domains. In the video, he uses Linux because the network interfaces are easier to remember. Once you’re done playing with DNS spoofing, remember to flush your local cache otherwise your browser will continue to go to the wrong IP.
[photo: mattdork]
Phlashing Denial Of Service Attack, The New Hype

Imagine how surprised we were to discover that by accidentally bricking our router we were executing a brand new attack: Phlashing Denial Of Service (PDOS). This week at EUSecWest, researcher [Rich Smith] will present the theoretical PDOS attack. Instead of taking over control of an embedded system, the attacker turns it into a nonfunctioning brick by flashing it with a broken firmware. Anyone who has flashed a device knows the danger of interrupting the procedure.
Continue reading “Phlashing Denial Of Service Attack, The New Hype”
Cat-5 Ethernet/Serial/PoE To Your Wireless Router
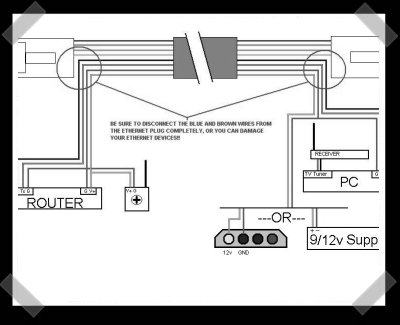
Adding PoE(Power over Ethernet) just wasn’t good enough for [steve]. Not only does he have power running over his Cat-5, he shared the ground wire and used the remaining pair to add a serial console to his rooftop mounted wireless router. Nice.










