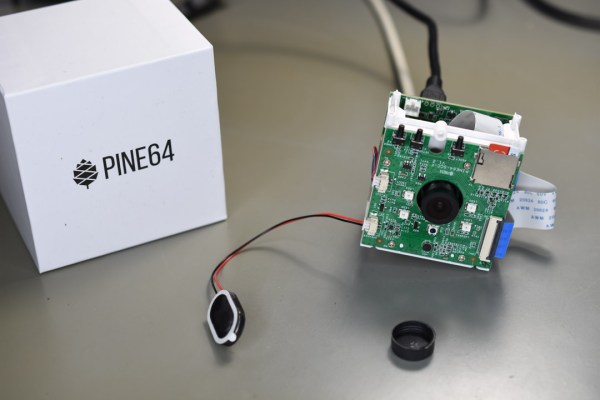
When the PineCube was announced by the Pine64 project in 2020, it created a fair bit of interest. Most of this was due to the appeal of a single-board computer (SBC) in a network-based (IP) camera form factor with integrated camera module, for a mere $29.99. Add an enclosure to it, and you would have a neat little package combining a 5 MP camera module with 100 Mbit Ethernet and WiFi. As a bonus, the system could be powered either via an optional battery pack as well as passive PoE, in addition to MicroUSB.
A few weeks ago I bought two of these boards, as part of a client project, and set out to use it for a custom IP camera implementation. With existing Linux-on-SBC and MIPI (CSI) camera experience on my end ranging from the Raspberry Pi to the Odroid, Orange Pi and Banana Pi boards, I felt fairly confident that I could make it work with minimal fuss.
Unfortunately, my experiences were anything but positive. After spending many hours with the PineCube, I’m not able to recommend it for those seeking an IP camera. There are many reasons for this, which I’ll try to explain in this article.
Continue reading “Hands-On With PineCube: An Open IP Camera Begging For Better Kernel Support”