Retro tech is cool. Retro tech that works is even cooler. When we can see technology working, hold it in our hand, and use it as though we’ve been transported back in time; that’s when we feel truly connected to history. To help others create small time anomalies of their own, [Dmitrii Eliuseev] put together a quick how-to for creating your own Advanced Mobile Phone System (AMPS) network which can bring some of the classic cellular heroes of yesterday back to life.
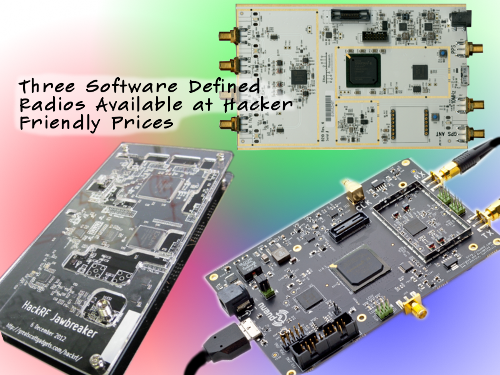
Few readers will be surprised to learn that this project is built on software defined radio (SDR) and the Osmocom-Analog project, which we’ve seen before used to create a more modern GSM network at EMF Camp. Past projects were based on LimeSDR, but here we see that USRP is just as easily supported. [Dmitrii] also provides a brief history of AMPS, including some of the reasons it persisted so long, until 2007! The system features a very large coverage area with relatively few towers and has surprisingly good audio quality. He also discusses its disadvantages, primarily that anyone with a scanner and the right know-how could tune to the analog voice frequencies and eavesdrop on conversations. That alone, we must admit, is a pretty strong case for retiring the system.
The article does note that there may be legal issues with running your own cell network, so be sure to check your local regulations. He also points out that AMPS is robust enough to work short-range with a dummy load instead of an antenna, which may help avoid regulatory issues. That being said, SDRs have opened up so many possibilities for what hackers can do with old wireless protocols. You can even go back to the time when pagers were king. Alternatively, if wired is more your thing, we can always recommend becoming your own dial-up ISP.