For those of us who worry about the security of our wireless devices, every now and then something comes along that scares even the already-paranoid. The latest is a device from [Samy] that is able to log the keystrokes from Microsoft keyboards by sniffing and decrypting the RF signals used in the keyboard’s wireless protocol. Oh, and the entire device is camouflaged as a USB wall wart-style power adapter.
The device is made possible by an Arduino or Teensy hooked up to an NRF24L01+ 2.4GHz RF chip that does the sniffing. Once the firmware for the Arduino is loaded, the two chips plus a USB charging circuit (for charging USB devices and maintaining the camouflage) are stuffed with a lithium battery into a plastic shell from a larger USB charger. The options for retrieving the sniffed data are either an SPI Serial Flash chip or a GSM module for sending the data automatically via SMS.
The scary thing here isn’t so much that this device exists, but that encryption for Microsoft keyboards was less than stellar and provides little more than a false sense of security. This also serves as a wake-up call that the things we don’t even give a passing glance at might be exactly where a less-honorable person might look to exploit whatever information they can get their hands on. Continue past the break for a video of this device in action, and be sure to check out the project in more detail, including source code and schematics, on [Samy]’s webpage.
Thanks to [Juddy] for the tip!
















hmmm… could this be used to remote control the computer e.g. after a certain idle time run a few keystrokes to open up a browser and send the captured data by url parameters/form?
While it might certainly take action and send keystrokes (the receiving portion likely being as broken as the sending portion), there is no way to capture on screen information using this device.
Unless it pressed ALT+PRINT and proceeds to send that image y remote controlling the browser (STRG+L in chrome for adressline-access for example). But then again: This would always be a blind manouver.
“Unless”??? Are you really asserting that yours is the only way?
“ALWAYS BE A blind maneuver”? Popping up a command shell and typing a simple “ping” command will INSTANTLY tell the attacker whether or not the attack is working.
Go ahead, make some more incorrect assertions.
Easy there F. I don’t think Indyaner meant that their method was the Only method. He offered one solution. No need to slap him down for it.
Why are people always so cunty on here?
Only the cunts are like that.
Wow – nasty much?
Welcome to the internet.
” there is no way to capture on screen information using this device.”
I’m glad I didn’t hire YOU as a security expert with your glib (and incorrect) assertions
Dude, chill. This is a blog. And the comments are here for the purpose of discussion. If you disagree offer a solution, don’t bash him.
if you can get a remote cmd shell open, who needs gui feedback? Even better, some kind of unix or kvm under control by it. I run microsoft (wired) keyboards on *nix systems because the ergonomics are great.
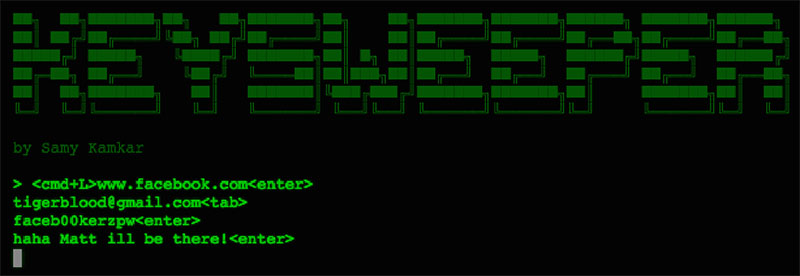
From keysweeper.ino:
// if you're looking at this, you found a secret function...
// this INJECTS keystrokes into a machine that uses a MS wireless keyboard ;)
// i will be releasing a project around this soon...
void tx(uint8_t* p, uint8_t key)
...
It seems more than a possibility to send keystrokes after seeing this.
As yet untested though.
Here’s how to obtain on-screen information with this device:
Have it set up either repeated print screens, or better yet, a video-stream over network to device owner’s IP. Congratulations, video feed established.
I think Jimmy’s point is that one could use this to transmit the captured key strokes back to a server or service on the internet using the victim’s own computer instead of having regaining physical access or relying on gsm. This certainly seems viable.
As others have pointed out, it might also be used to download and install additional malware such as a reverse-shell that allows an attacker to gain much more control and access to the victim’s computer (including being able to capture the screen).
The whole point of this device is to remain hidden. There are many situations at my job where a PC might sit idle for several minutes or longer. Much longer if this thing is sensing just keyboard input and not KB and mouse.
Point is, a user is going to realize something is wrong if a command window pops up with a ping or the web browser appears and weird address are being typed in. They’ll think “trojan” of course but if it keeps up they’ll home in on the culprit or realize the wireless keyboard is a problem and swap it out for a wired version. They’ll figure it fast if their tech support reads HaD (not likely but it’s possible).
No… a smart hacker would keep it on the down low and get the data some other way. Direct connect via Wireless network would be good.
I think you give most computer users a little to much credit. The first thing I think when I get a random shell that opens and then quickly closes on my work PC is that the IT group just triggered something. Hunting what they trigger via batch scripts is not really my job description so I’d keep on working. If it happened at home then I’d be suspicious and start hunting.
For this particular hack, I would never be a victim anyway. Work only allows wired keyboards and I only use wired keyboards at home.
Depending on the wiring of the building you could use something like a HomePlug powerline whatsits to send data over the power lines (hey it is plugged in) to a data logger hidden somewhere else in the building.
If the office leave the machines on 24/7, a trojan can easily do it work in the after hours when nobody is around.
With a good enough antenna, the dongle doesn’t even have to be hiding in the office.
Or just open the browser to a shock porn site.
I bet it still can be used as a charger too !
I bet it does too, or it would be very quickly discovered.
The internal guts of the charger is kept. So, yes, it still works as a boring harmless USB charger.
This is what I was wondering as well!
Not much of a surprise considering the content. However WARNING the samy.pl website linked above contains a virus.
That being said I love the detailed guide for building this sniffer.
This is a fine example of how much Microsoft takes security seriously, the safe assumption is that all of their products have similar issues.
Why just bash MS?
Is there any proof, that all the other manufacturers of wireless input devices are any better?
The capability or inclination of other manufacturers to do better does not make MS keyboards any less insecure.
Having just bought some new Logitech hardware, I was curious about this. They seems to do it right with their “Unifying” platform. They used AES-128 for encryption and generate a shared key between receiver and device during pairing…. meaning an attacker is unlikely to break the encryption scheme unless they’ve sniffed the pairing process or maybe have physical access to the device or receiver (but I don’t know the details of the Unifying hardware).
See: http://www.logitech.com/images/pdf/roem/Advanced_24_Unifying_FINAL070709.pdf
Exactly my thought. Why is Microsoft so dumb about this?
“Thorsten and Max discovered the keystrokes are simply encrypted (xor’d) with the MAC address in ECB mode, which we are able to sniff after using Travis’ method of abusing the nRF24L01+ to both sniff and reveal MAC addresses. This “encryption” is the equivalent of taking a deck of cards, cutting it once, and calling it shuffled.”
Indeed, but bear in mind that the Micro$oft K/B is probably outsourced to some 3dr party, so the chances are this kind of hack works on a bunch of different venfors products. Furthermore, stick a Micro$oft duff RF K/B on your Linux fortress and it will be pwned just as quickly.
Me… I’d be happy if there was an EDIT BUTTON ON THIS BLOG… s/venfors/vendors/g ^^^
I hate to make assumptions, but I’d guess any basic RF keyboard has a similar issue. They likely picked some of the shelf solution. I don’t know if Bluetooth is any more secure.
I would trust Bluetooth much more than any proprietary RF protocol. For one, BT requires pairing. It is PITA but makes it a lot more secure.
BT is vulnerable to the same styles of attacks as WiFi. You can force un-pairing or promiscuous mode and gain control of devices.
Logitech has it figured out, it seems. See: http://www.logitech.com/images/pdf/roem/Advanced_24_Unifying_FINAL070709.pdf
This isn’t limited to Microsoft keyboards. Your comments are beginning to resemble trash
I think this is more a question of technology advancing to make previous technology obsolete rather than a specific failing of Micro$oft. When the Redmond subcontractors were tasked with producing a wireless keyboard, their brief was “we will sell it for X dollars”, not “this has to have world class security in case someone invents an rf sniffing arduino based wall wart”. Now the RF sniffing wall wart exists, then we can expect a keyboard to be produced in a few years that combats this hack… Once the current stocks run down and the ‘dwigno device becomes common place, gets mentioned on Fox News or whatever, that will be the time for Mixro$oft to spend a few more hours of development time changing the security.
So you have the U/P for the computer thanks to this.
The user presses the power down button on the keyboard and is gone for the day.
The device waits for an hour or so, then sends the power on command, logs in, opens a reverse VPN and during the night you own the network.
And they’d never know…
assuming they have wake on keyboard set in the bios, sure.
I make a point of turning all of the wake on’s off in the bios of any computer I use… seems like a bit of a hole.
And people wonder why I prefer wired equipment, rather than wireless. :D
I’ve refused to use them since the first USB ones came out. I simply could not figure out how they could implement a solid encryption of the data from device to host on the thin margin that cheap keyboards existed at. It’s been harder to convince others of the issue since everything went from 900MHz (which you could some times hear transmitting with a wireless phone) to channel hopping 2.4GHz devices.
And every time you approach your machine, and before you enter a single password, you no doubt check to see if your keyboard has a keystroke logger installed.
Google for KeyGhost if you want to see some easily available commercial offerings; there are also plenty of roll-your-own loggers including the open source NSA Playset at http://www.nsaplayset.org . Some are bare-board and are designed to be hidden inside your keyboard. And if you want to see what the pros use, check out the NSA ANT catalog for devices like COTTONMOUTH, HOWLERMONKEY, and SURLYSPAWN.
If an attacker wants to monitor your keystrokes badly enough, he’s going to find a way.
By the same reasoning, you might as well never bother locking the doors to your house and car, as any real pro is going to be using devices such as ROCK, BRICK, LONGPOINTYCROWBAR, REGULARCROWBAR, and BIGSTICK.
Security is selected and implemented by degrees.
Google —> site: hackaday.com “edit button”
About 3,860 results (0.47 seconds)
HAD… a blog that listens to its contributers.. }:¬)
i was just re-reading this article and thought…
if H.A.D. had an edit button,
you know what would happen?
think for a second…
the site is called HACK-a-day.
some people would take it as a challenge to hack edit functionality.
i bet cash(edit:e-currency) it would be broken in only a few hours,
maybe minutes?
… i mean, its wordpress, a BLOG company,
they have no desire for being the most secure.
even blogger/google-blog got PWNED for an entire day.
theres a reason we dont have edit buttons here, because putting
an edit button on HAD will end up getting wordpress to dump us!
(after the whole interwebs worth of wordpress gets hacked)
2009… We’ve been asking for at least Six YEARS for an edit button…
http://hackaday.com/2009/04/20/fast-little-hexapods/#comment-71313
…cruel and unusual punishment by anybodies standards (well… by mine at least)… I have half a mind to start a petition on change.org about this.. }:¬(
MOD EDIT: What are you talking about again?
The problem with an edit button is you need an account to log into, so ypu can verify that you are editing your own comments. On the other hand, now they could just integrate with Hackaday.io accounts for commenting.
That’s actually not true. There are other models such as using a unique user name that you keep private but is converted automatically to a public hash that is visible to other users. That way users don’t have to go through the process of creating an account, but it still creates a continuity as the same person makes more comments over time.
So you have a public name you sign your posts with and a secret name you use to authenticate that you are you? How is that different from login and password setup?
The password is private. The public hash can be reversed with Rainbow Tables…. in theory anyways.
Derp, reply, not report.
So it’s a bad login/password system that requires users to compare the hashes to see that this “MikrySoft” is indeed the same “MikrySoft” that posted earlier? Thanks, but no thanks.
This. If a hackaday.io account offered me the “feature” of editing comments, I would instantly create one.
Some context some opinion:
For years, Hackaday was owned and run as a hobby by a many-millionaire who had real businesses and new startups to run on the side. During that time he made basically zero changes. He didn’t appear to bother having a marketing plan, threw some adwords on it, and made (he figures) about 17% of what he could have if he would have bothered to put effort into it.
Why for the last 5 years was an edit button not added? Why does it seem like no one really gave a shit? Probably because it was no one’s job to make the site better, and the person in charge didn’t give a shit because it was mostly a hobby.
Then it got sold last year to an electronics advertising company. They presumably do care about maximizing the amount of money they can get from the site, because they didn’t buy it for charity.
Adding an “edit” button requires a few things:
1 – Someone to actually make that decision. I don’t think we have any full time employees.
2 – Someone who’s job it is to grow the company. I don’t think we have that person. Hackaday did throw some money to create a project sub-site that is.. as good as it is. They threw money at a new website that is… as good as it is. A webstore that is… as good as it is. They also threw $200k (110% of a whole year’s income according to the previous owner, including contributor pay, editor pay, hosting, and all pocketed profit), at a contest to not send anyone into space. All these things, spread the existing part timer people who ran the place very thin.
3 – Having an edit button make sense. As you can see from comments every time it comes up, it’s not a given thing that it makes things better. Just because people ask for it does not mean it is a good idea. Maybe it does get thought about but axed.
4 – Having a community that is worth investing in. Not just in the type of people, but in the amount of them. Hackaday used to have (apparently still has, unlinked) forums. They’ve basically always been a ghost town. So by observation, this isn’t really a place people go to participate, it’s a place they go to digest then depart.
5 – Having budget to make the changes. We don’t have accounts, it’s not just a few clicks to add. Is it going to result in more pageviews? Is the corporate owner going to justify the decision-making process and the implementation? Is the person who has to ask the corporate owner going to ask for that, with how busy they are? What priority are the comments in the articles, and by what magnitude are they improved by adding an edit button?
6 – Having someone to actually make the changes. The website launch went… as well as it did. When errors were found, they took… as long as they did to be fixed.
7 – Having nothing else better to do it one is to spend time/effort. Hackaday is planning new stuff this year.
…
I mean, you could always do what I did. I got a job here just so I could have an edit button for my posts. Look at me, making any edits I want. Na na na na na. U jelus bro?
Just wanted to add…
Apparently my edit button only appears on my own articles. Which this isn’t. So, that typo up there shall remain.
I have a feeling I’m going to have to buy the company to get it, and damned if I’m sharing with the rest of you when that happens.
LOL
Re: #4 – the comment section *is* the forum. People aren’t going to dig around to yet another site, because the discussions happen here, among the posts.
That’s true, but each is suited to their own.
If a reader wants to comment on a story, it makes sense to do it in the article comments. It would be weird to go off to create a forum thread about it.
But if a reader wants to create something of their own, or their own topic, that obviously doesn’t work on the comments section of some article.
It just says to me that the participating community, in either venue, is probably rather small and there’s minimal return on improving the experience. At least in terms of what are the biggest targets, improving the commenting experience probably isn’t extraordinarily high.
A big comment thread here is like, 30+ posts. Average is probably closer to 10. It’s not like Reddit where the comments get ballpark same views as the source.
Unless the reason holding back the comments from being more successful is the lack of edit button, I can see why it’s never been something that’s gotten around to.
since it is already plugged in the wall, time to go back to using pre-existing electrical wiring as a conduit for data transfer, so multiple devices can collaborate.
The wallwart device could emit the binary stream of a malicious executable file into notepad (for example) and save it, then run it. That exe could find some juicy data on the PC and send it back (slowly) to the wallwart by simply encoding the data as a series of and toggles (grey code or some such). Then delete the exe. As many (most?) wireless keyboards don’t have numlock/capslock LEDs nobody would notice unless they are actually sitting there entering keystrokes at the time.
Recovering the pilfered data would be another question altogether of course.
So don’t use wireless keyboards.
^^^ typo: “and toggles” should have been “capslock and numlock toggles”. Sorry.
The underlying exploit is know since 2010/2011 (see links in original article). I hope this nicely executed packaging will finally bring the necessary attention to this issue.
afaik exploitable keyboards (specific microsoft model) are no longer on the market
define ‘on the market’
what really scares me is the fact that in 2015 people are still dumb enough to use wireless keyboards. no wireless encryption will ever be secure so long as there are people out there with enough time on their hands to break it.
Actually with proper encryption a keyboard should be pretty secure. Take logitech’s AES128. You could guess the key, but, but that will take too much time to be practical with anything. The problem here is that Microsoft did not bother to do any serious encryption…
Had anybody considered that this device may be used for security as opposed to infiltration? It appears that the blinking led function may serve to alert the keyboard owner if someone is using his keyboard, and the logger to see what people where up to whilst he is afk. I find this a brilliant hack.
is there a charging circuit for that LiPo battery ?
It’s included on the GSM board, was wondering the same thing myself.
It’s 11:00. Do you know where your chargers are? A bit of prudence about security should include a periodic check to be sure nothing “extra” has been plugged into the back of one’s computer, and knowing where and what all your wall warts are. Ideally, not having them plugged into outlets down behind the couch or hidden under a table.
am i in bold?
Am i in red?
Real ninjas just replace the wall outlet with “spare parts”, so it’ll be a just a drive by ninja attack.
Everyone. I would like to apologize for my earlier behavior. After some time to reflect I realize that my statements did not contribute to the nature of the post. My intent was only to critique what I thought was a purposefully incorrect statement, and I see how I misread what was being said.
To avoid remote C&C olny you can do is logs into pc with smard card and lock that pc by remove this card
people is still amazed that Microsoft has no clue about security?
ah ah ah
One more reason to never use anything Microsoft. Their history of security flaws should be enough warning but people don’t want to hear what they don’t want to believe.
how many chinese keyboard have sniffer inside?