[Micah Elizabeth Scott], aka [scanlime], has been playing around with USB drawing tablets, and got to the point that she wanted with the firmware — to reverse engineer, see what’s going on, and who knows what else. Wacom didn’t design the devices to be user-updateable, so there aren’t copies of the ROMs floating around the web, and the tablet’s microcontroller seems to be locked down to boot.
With the easy avenues turning up dead ends, that means building some custom hardware to get it done and making a very detailed video documenting the project (embedded below). If you’re interested in chip power glitching attacks, and if you don’t suffer from short attention span, watch it, it’s a phenomenal introduction.
Spoiler: the ROM dump comes out in the USB device enumerator strings. Using a Chip Whisperer (second place in Hackaday Prize 2014!) and the “FaceWhisperer” add-on board of her own design, [Micah] could send power-supply glitches just as the tablet was identifying itself to the computer. Instead of stopping after the few device descriptor bytes, it just kept on going. And going. In fact, in one of the many brute-force attempts, it dumped its ROM twice, making it easy to find the beginning and end of the code stream.
Next up is disassembling and reversing the software, which is no small feat. We can’t wait to see what [Micah] comes up with.
Thanks to [Ben] and [Tim] for the nearly-simultaneous tips.

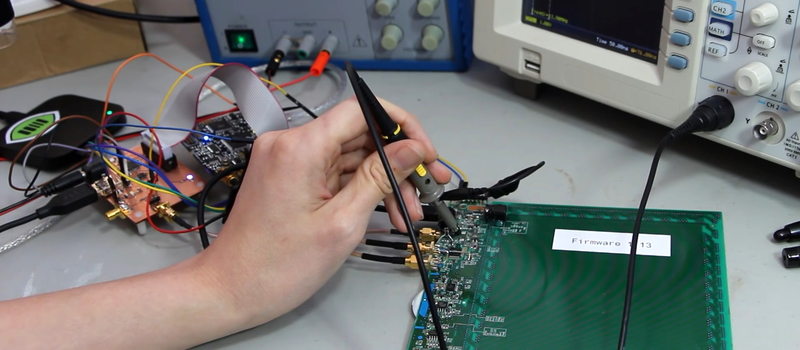














Maybe look at the old palm pilot wacom emulation utilities for clues.
Hadn’t heard of the Palm Pilot stuff, but I did look at linux-wacom. Most of it hasn’t been reversed to a deep level; they have some canned requests that put specific tablets into their featureful modes, but my reversing so far has already turned up lots of stuff that is nowhere in any of the public drivers I’ve seen.
Ohh wow that is an interesting little trick!
A trick as old as digital circuits goes that anyone who learnt about the need of decoupling caps should know well, but now thanks to modern tools affordable to anyone without all the cumbersome custom work.
Back then we started glitching counters in LED clocks, now they glitch registers of highly complex SoC.
The beauty is in the implementation and the superb detailed explanation from some so knowledgeable!
Yeah. Used to be really popular with people who wanted free pay TV back in the day. I believe some of the glitching setups were actually surprisingly cheap back then.
I used to do something similar, as did friends, with Atari 2600 cartridges: flip the power switch quickly and get things like unlimited lives, lots of points and other things.
Went for shift and hit enter instead….
Even did it on some of the Atari computers and other consoles that used cartridges.
I am consistently amazed by the work Micah does – every video full of useful info and incredibly well put together. And this trick looks like it could come in very useful for all sorts of devices.
Neat, nice work.
If you follow her twitter you’ll see she spends over a week editing and creating excellent work. Thankyou mikeselectricstuff for turning me onto a great mind… HaD took you long enough -,,.- jk njk nnjk < jk !jk messing
.. btw. I bought a bamboo tablet last week because of this
The work she puts into the video shows, it’s polished and information dense at a reasonable pace. That work plus some talent makes for an excellent result. Just the right measure of knowledge for those new to an area of knowledge. There will always be some that complain about the level of detail but those people are the ones you don’t want to ask questions. Nice setup by the way.
“HaD took you long enough” :)
She’s been a judge for the Hackaday prize, and we’ve covered [scanlime]’s hacks since the ATtiny RFID tag hack of 2011, and were probably one of the first outlets to run a story on her coastermelt project.
Heck, I wrote up a section on her fadecandy board in my writeup on driving RGB LEDs, but it got cut due to space constraints. It’s still the most sophisticated color driver board/system I’ve ever seen.
And her vids are all _amazing_. Respect!
Your automatic response proves that the vast majority of any comment section is just angry nonsense. I was having a friendly joking poke not at her never being featured (as I’ve been following for years, both HaD and Micah) only that this wasn’t posted 2-3 days ago when it was released. “!jk jk” ect. Maybe I’m not as funny as I thought I was or possibly a little sleep deprived at the time but c’mon I don’t need the well written detailed oversight of what you’ve done. I’m removing myself from all future interaction from this fine establishment. My apologies
Chill dude – you seem to be over-reacting to something or other.
I see nothing angry in there. You are projecting.
I love how she was able to fit the whole process into a 36 minute video. Wonderful to see this kind of commitment into a hack and documentation.
I had only heard of side-channel attacks, but never saw one in action, and had no idea of the extent of control that is possible by simply glitching the power supply (very precisely).
Great entertainment and information, thanks!
This was an awesome hack. Props!
This is amazing.
So does the software that’s used starting from 11:23 delivered together with the Chipwhisperer?
Looks like the protocol reverse engineering software is Total Phase, worth thousands of dollars: http://www.totalphase.com/store/
thanks, I didn’t know of that software. When you say “worth” thousands of dollars, do you mean it costs less but is worth more? They do sell some pretty expensive stuff, and stuff they don’t mention the price off, which is usually a sign of bad things to come!
Actually I have no idea. Maybe the software is free, but the special hardware listening/decoding attachments cost the money?
http://www.totalphase.com/products/beagle-usb12/
It sure is slick software.
This is way too complicated for me but really awesome. If you are interested in reverse engineering and stuff like that you really should have a look at the other scamline-videos of this women (what’s the female equivalent of guy?)! https://www.youtube.com/user/micahjd/videos The 2 Coastermelt-videos are really impressive.
I think the word you are looking for is gal. Happy hacking!
Is dude gender neutral?
(dudette?)
Very interesting! I bought a used Wacom tablet thingy for next to nothing at a local Goodwill store. Wacom has a habit of not supporting older models with the latest Windows version so they end up in thrift stores and landfllls. I also came across one of the hugely expensive porfessional desktop sized models for a mere 20 euro. Didn’t have the essential pen though so i had to pass.
Don’t I know it. I have a couple of 12 x 12 inch tablets, serial port only. So they are a bit thick and hefty, but I’d still use them. No such luck, Wacom dropped support for them long, long ago.
You’re lucky with the serial-only ones… they have a pretty standard interface and that info is all over the internets, if you can’t figure it out via hyperterminal, etc.
There are tons of projects to make them useful, but maybe less-so in the Windows-realm. MacOS has TabletMagic, Linux has support, and more… Throw in a USB-Serial dongle and your endeavors are *much* easier than glitching firmware via USB…
And if you’re looking for a hack-job, the wacom-digitizers in most windows-machines’ LCDs are 3.3V serial, as well… though their protocols sometimes vary slightly, it’s usually not too difficult to figure out.
Unfortunately all I want to do with them is be able to use them in Paintshop Pro and Corel. I’m no programmer, my favorite programming language is solder.
Check out WaxBee converter. All You need is Atmega32U4 with right firmware. Now any serial tablet can mimic standard Intuos 5 USB interface.
More info on forum: http://forum.bongofish.co.uk/index.php
Very impressive work, and well presented too! Thanks for sharing.
I’ve seen this done with old embedded gaming devices and calculators to dump roms. It works like a user-after-free attack but you use the clock control to make it happen and sometimes it’s a use-before-free.
Wow, I’ve heard of things like this, glitching, and remember, (now that it’s been mentioned) getting some interesting effects from quickly power-cycling vid-games… But to pin it down to anything less than random, to use it for actual dumping of the ROM (or even just increasing your vid-game’s lives) seems like it’d be nothing but chance. Even with precision-timing. There’re interrupts and context-switching, timers whose values will never be the same between consecutive glitch-runs, plausibly a core that runs at a different speed than the memory-accesses… There’s a ton of amazingly precise science going on here, but then, the USB descriptor mightn’t’ve been loaded from ROM, at all, but plausibly from static variables… in which case not a ROM-dump, but a RAM-dump. Or maybe a different memory-space entirely (eeprom?). And, if that weren’t enough, what’s causing that counter to go sequential in the first place… we’ve already glitched it to the point of skipping its end-point, one variable/instruction destroyed, how do we know this thing is outputting data sequentially at all? It’s like using tremendous amounts of highly sophisticated scientific equipment to locate a unicorn. And yet, from the sounds of it, it’s not only been done, but people do it somewhat regularly. Wow!
Mind-Boggled.
You should look how similar CPU clock dumps are to ring-0 vulnerability exploitation on x86. It’s mostly DMA and interrupt-changes so even if you find something it’s usually impractical to exploit reliably.
Micah is a real life Jennings (Ben Affleck) from Paycheck (2003) :o
this is so cool! Great video – thanks!
After already being blown away by the awesome video, I then see that her cat has thumbs and can play fetch.