Neural networks are all the rage right now with increasing numbers of hackers, students, researchers, and businesses getting involved. The last resurgence was in the 80s and 90s, when there was little or no World Wide Web and few neural network tools. The current resurgence started around 2006. From a hacker’s perspective, what tools and other resources were available back then, what’s available now, and what should we expect for the future? For myself, a GPU on the Raspberry Pi would be nice.
Day: April 24, 2017
White-hat Botnet Infects, Then Secures IoT Devices
[Symantec] Reports Hajime seems to be a white hat worm that spreads over telnet in order to secure IoT devices instead of actually doing anything malicious.
[Brian Benchoff] wrote a great article about the Hajime Worm just as the story broke when first discovered back in October last year. At the time, it looked like the beginnings of a malicious IoT botnet out to cause some DDoS trouble. In a crazy turn of events, it now seems that the worm is actually securing devices affected by another major IoT botnet, dubbed Mirai, which has been launching DDoS attacks. More recently a new Mirai variant has been launching application-layer attacks since it’s source code was uploaded to a GitHub account and adapted.
Hajime is a much more complex botnet than Mirai as it is controlled through peer-to-peer propagating commands through infected devices, whilst the latter uses hard-coded addresses for the command and control of the botnet. Hajime can also cloak its self better, managing to hide its self from running processes and hide its files from the device.
The author can open a shell script to any infected machine in the network at any time, and the code is modular, so new capabilities can be added on the fly. It is apparent from the code that a fair amount of development time went into designing this worm.
So where is this all going? So far this is beginning to look like a cyber battle of Good vs Evil. Or it’s a turf war between rival cyber-mafias. Only time will tell.
Laser Surgery: Expanding The Bed Of A Cheap Chinese Laser Cutter
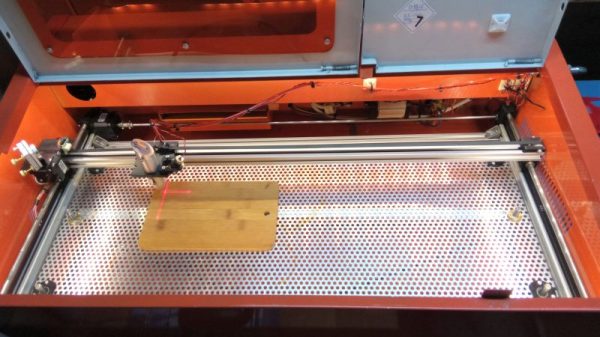
Don’t you just hate it when you spend less than $400 on a 40-watt laser cutter and it turns out to have a work area the size of a sheet of copy paper? [Kostas Filosofou] sure did, but rather than stick with that limited work envelope, he modified his cheap K40 laser cutter so it has almost five times the original space.
The K40 doesn’t make any pretenses — it’s a cheap laser cutter and engraver from China. But with new units going for $344 on eBay now, it’s almost a no-brainer. Even with its limitations, you’re still getting a 40-watt CO2 laser and decent motion control hardware to play with. [Kostas] began the embiggening by removing the high-voltage power supply from its original space-hogging home to the right of the work area. With that living in a new outboard enclosure, a new X-Y gantry of extruded aluminum rails and 3D-printed parts was built, and a better exhaust fan was installed. Custom mirror assemblies were turned, better fans were added to the radiator, and oh yeah — he added a Z-axis to the bed too.
We’re sure [Kostas] ran the tab up a little on this build, but when you’re spending so little to start with, it’s easy to get carried away. Speaking of which, if you feel the need for an even bigger cutter, an enormous 100-watt unit might be more your style.
Continue reading “Laser Surgery: Expanding The Bed Of A Cheap Chinese Laser Cutter”