[Haseeb] failed the marshmallow test as a kid. He has no self-control. He wastes a lot of time on reddit. There is a solution to this problem — simply lock yourself out of your account. The process is simple, and all you need to do is change your password to something random, change the recovery email address, and click submit. In the blink of an eye, all your imaginary Internet points vanish.
That’s the one guaranteed way to quit reddit. However, [Haseeb] wanted to hold onto those magic Internet points in the event they become worth something. This led to a far more baroque solution. He found a service that would email him at a later date, send an email to himself containing a random password, and quit reddit temporarily. Until that email was delivered, he was officially off reddit. When that email was received, productivity would stop.
A few years pass, and [Haseeb] had some time to kill at his new job. He decided to scrounge up his old password, only to discover he locked himself out of his Reddit account until 2018. What followed is a security exploit of an ’email me in the future’ service, and a great example of how much effort one person will commit to a lifetime of instant gratification.
The email service in question is LetterMeLater, a site that will send an email at some arbitrary point in the future. You can hide the body of the email from yourself, making this a fairly good solution for what [Haseeb] is doing. He was still locked out of his email, though, and emailing the people running LetterMeLater seemed absurd. Dopamine is fun, though, and [Haseeb] eventually found a workaround. This site indexes the body of an email for search. This is great, because the body of the email this site would send [Haseeb] in 2018 contained his reddit password and only his reddit password. With a little bit of code, he can perform substring queries on an email he can’t read. Now, extracting the password is simply a first year CS homework problem.
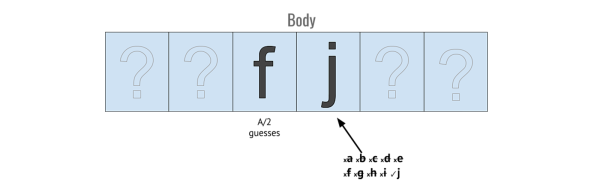
At this point, the only thing [Haseeb] knows about his password is that it’s a long string of random characters that probably doesn’t include upper-case characters. That’s 26 possible characters, 10 possible numbers, and a character bank that can be determined by searching his email one character at a time. [Haseeb] is essentially playing Hangman against his former self here.
After figuring out an API for LetterMeLater, [Haseeb] whipped up a quick bit of code that finds the password by searching substrings. It’s beautiful and recursive, although he did break it down into finding a suffix of the password then determining the remainder of the password. It took 443 iterations of the code to find the password, and when that was complete he logged into reddit. Math works, although [Haseeb] will have to figure out a way to wean himself off the opiate of the millennials again.