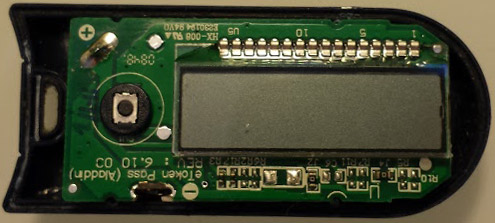
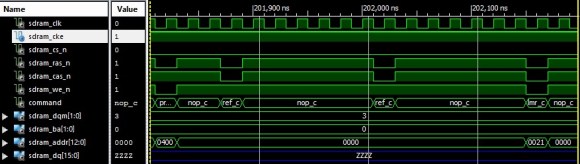
One-time passwords (OTP) are often used in America but not so much in Europe. For our unfamiliar readers, OTP tokens like the one shown above generate passwords that are only valid for one login session or transaction, making them invulnerable to replay attacks. [Dmitry] disassembled one eToken (Aladin PASS) he had lying around and managed to reprogram it for his own needs.
Obviously, these kind of devices don’t come with their schematics and layout files so [Dmitry] had to do some reverse engineering. He discovered six holes in a 3×2 arrangement on the PCB so he figured that they must be used to reprogram the device. However, [Dmitry] also had to find which microcontroller was present on the board as its only marking were “HA4450” with a Microchip logo. By cross-referencing the number of pins, package and peripherals on Microchip parametric search tool he deduced it was a PIC16F913. From there, it was just a matter of time until he could display what he wanted on the LCD.
We love seeing tiny consumer hardware hacked like this. Most recently we’ve been enthralled by the Trandscend Wi-Fi SD card hacking which was also one of [Dmitry’s] hacks.