Normally, when we talk about video games having bugs, it’s some kind of item duplication glitch or a hilarious failure in the jacket equip code of some tedious first-person-shooter online wardrobe simulator. Counter-Strike 2 has had a more embarrassing faux-pas, however, with a security hole allowing bad actors to theoretically capture the IPs of their fellow players in a server. You won’t believe how this came to happen.
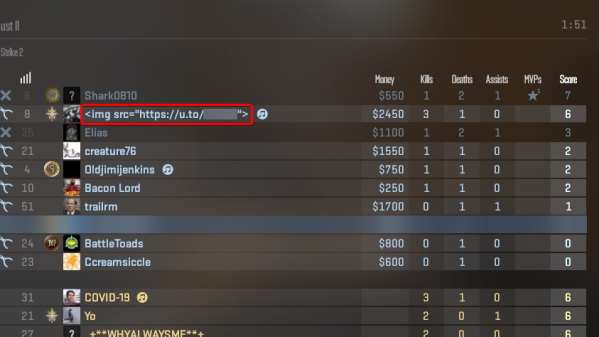
The exploit has already been making its way around the forums, with one [Crouch9706] raising the alarm. It’s all down to the way Counter-Strike 2 renders the names that players have entered in their Steam gaming profiles. In certain menus and other parts of the UI, the game will actually parse HTML in a player’s name. Typically, the way to trigger it is to join a game and vote to kick yourself. This brings up a dialog for other players that shows them your player name and parses the HTML. The only limitation is you only get 32 characters for your HTML.
There’s a nifty little extra trick to this, though, in that you can use this technique to snag another player’s IP. By putting in HTML that links to your own server, you can log any player IPs that connect to the server seeking an image, for example.
Of course, it’s not the biggest risk, with many players being behind ISPs that use CGNAT, making the harvested IPs rather useless. However, this sort of unexpected code injection is really not acceptable from a security standpoint. At the very least, it has the potential to expose players to nasty imagery.
Word on the street (Nitter) is that the exploit has now been patched. Meanwhile, if you’re working on a game that for some mad reason, executes code based on player names or any other such data, consider patching your work ASAP. If you find similar exploits in the wild, don’t hesitate to hit up our tipsline—and notify the developers, too!