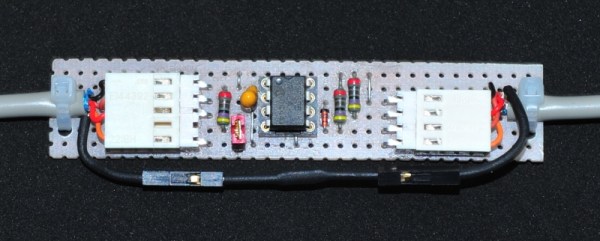
If you got an old PC/XT stored somewhere in basement and want to use a newer keyboard, here’s a little project you might like. [Matt] built an AT2XT keyboard adapter on a prototype board using an AT to PS/2 keyboard cable. An AT2XT keyboard adapter basically allows users to attach AT keyboards to XT class computers, since the XT port is electronically incompatible with PC/AT keyboard types. For those retro computing fans with a lot of old PCs, this trick will be great to connect the XT machines to a KVM (keyboard/Video/Mouse) switch.
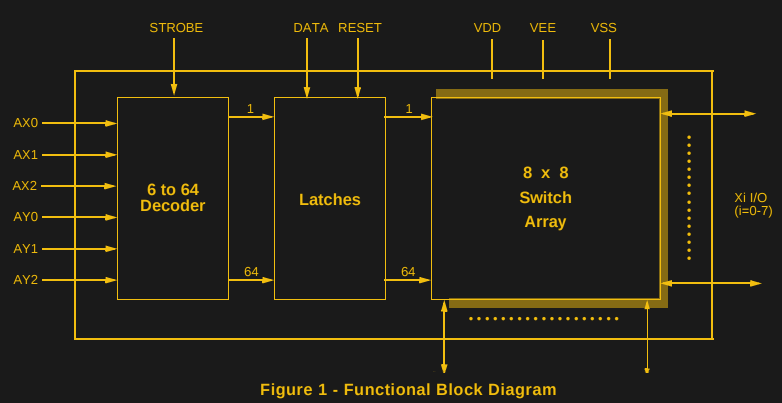
[Matt] found schematics for the project on the Vintage Computer Federation Forum, but used a PIC12F675 instead of the specified PIC12F629. He does provide the .hex file for his version but unfortunately no code. You could just burn the .hex file or head up to the original forum and grab all files to make your own version. The forum has the schematics, bill of materials, PCB board layout and firmware (source code and .hex), so you just need to shop/scavenge for parts and get busy.
And if you are felling really 31337, you can make a PS/2 version of the binary keyboard to justify the use of your new adapter.
[via DangerousPrototypes]