Antenna tuning at HF frequencies is something that radio amateurs learn as part of their licence exam, and then hone over their time operating. A few basic instruments and an LC network antenna tuner in a box are all that is required, and everything from a bit of wet string to ten thousand dollars worth of commercial antenna can be loaded up and used to work the world. When a move is made into the gigahertz range though it becomes a little more difficult. The same principles apply, but the variables of antenna design are much harder to get right and a par of wire snippers and an antenna tuner is no longer enough. With a plethora of GHz-range electronic devices surrounding us there has been more than one engineer sucked into a well of doom by imagining that their antenna design would be an easy task.
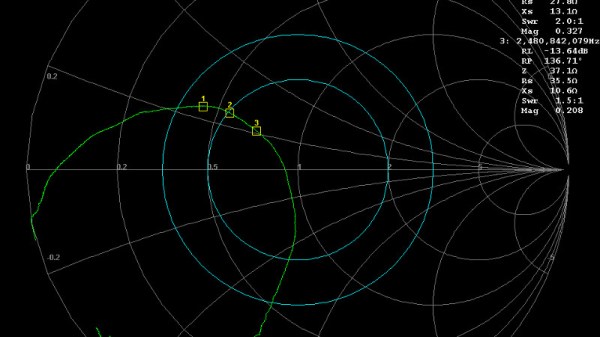
An article from Baseapp then makes for very interesting reading. Titled “Antenna tuning for beginners“, it approaches the subject from the perspective of miniature GHz antennas for IoT devices and the like. We’re taken through the basics and have a look at different types of antennas and connectors, before being introduced to a Vector Network Analyser, or VNA. Here is where some of the Black Art of high frequency RF design is laid bare, with everything explained through a series of use cases.
Though many of you will at some time or other work with these frequencies it’s very likely that few of you will do this kind of design exercise. It’s hard work, and there are so many ready-made RF modules upon which an engineer has already done the difficult part for you. But it does no harm to know something about it, so it’s very much worth taking a look at this piece.
It’s an area we’ve ventured into before, at a Superconference a few years ago [Michael Ossmann] gave us a fundamental introduction to RF design.