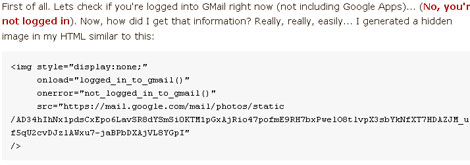
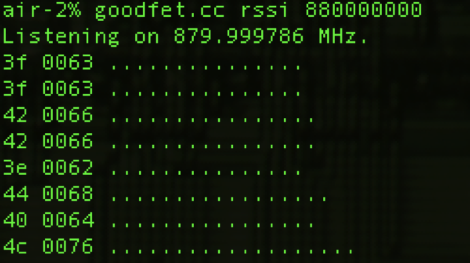
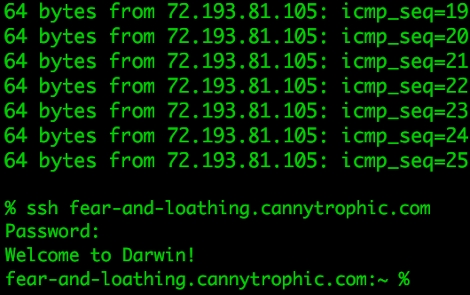
One of the most fun aspects of a LAN party was exploring the shared files of all the other users on the network. There were people that would show up, solely for the file swapping. That is exactly what this project is about. From the projects wiki, the Pirate box is a mobile p2p sharing and collaboration platform. Basically it is a wireless hotspot with a slick interface and a shared folder. It doesn’t connect to the internet, and it doesn’t log any connections. You can have a file swapping session simply by flipping it on and sharing its space with other people. They’ve included a step by step guide to setting up your own, but if you’re going to do some subversive file swapping we might suggest putting it in a less conspicuous enclosure. Imagine this as a portable verion of dead drops.