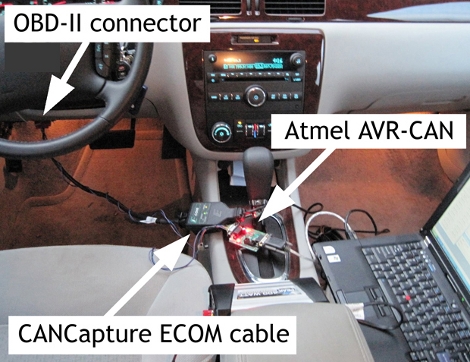
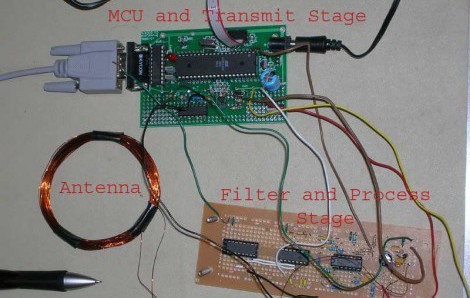
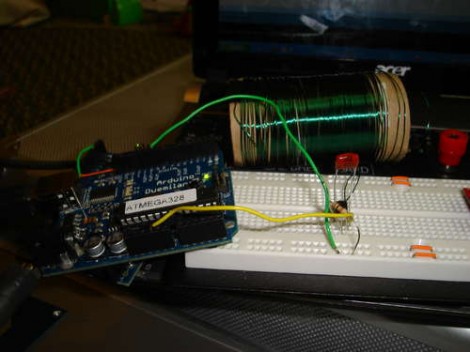
Do not put anything in this box that you will need in a rush. You’ll have to successfully guess the word in a game of hangman to gain entry. He’s using an Atmega328 as the brains of this project with a rotary dial and an LCD for input and display. If you win, the box is unlocked and you can open it up to get whatever is inside. There are links to various tutorials along the way to help with each step, including the Arduino source code he used to build it. We think he should bump it up a notch and have the box destroy the contents if you fail. Sounds like fun, right?