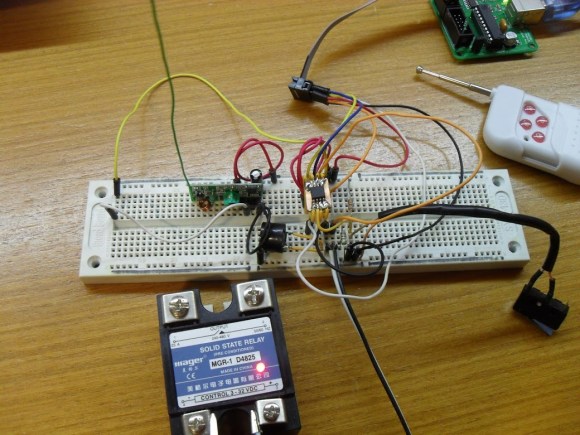
This breadboarded circuit is [Sergio’s] solution to controlling appliances wirelessly. Specifically he wanted a way to turn his pool pump on and off from inside the house. Since he had most of the parts on hand he decided to build a solution himself. What he ended up with is an RF base station that can learn to take commands from different remote devices.
The main components include the solid state relay at the bottom of the image. This lets the ATtiny13 switch mains voltage appliances. The microcontroller (on the copper clad square at the center of the breadboard) interfaces with the green radio frequency board to its left. On the right is a single leaf switch. This acts as the input. A quick click will toggle the relay, but a three-second press puts the device in learning mode. [Sergio] can then press a button on an RF remote and the device will store the received code in EEPROM. As you can see in the clip after the break, he even included a way to forget a remote code.
Continue reading “RF Switching Module Can Learn New Remotes”

 While playing chiptunes, creating lightning, and illuminating fluorescent tubes with a homebrew Tesla coil is awesome, they’re not exactly the safest electrical devices around, and certainly aren’t easy or cheap to build. There’s another option open if you’d like to play with strong electromagnetic fields;
While playing chiptunes, creating lightning, and illuminating fluorescent tubes with a homebrew Tesla coil is awesome, they’re not exactly the safest electrical devices around, and certainly aren’t easy or cheap to build. There’s another option open if you’d like to play with strong electromagnetic fields;