Both our electrical meter and our gas meter are located in the basement of our house (we recently had the gas meter moved outside though). When people see this they always ask if the meter readers have to come inside once a month. The answer is no, these meters broadcast usage data which is picked up once a month when a utility company vehicle drives down the street. If you have wireless meters in your house, here’s a way to harvest and graph the wireless data so that you can analyze your usage patterns.
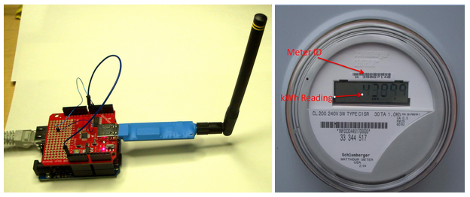
The hardware used here is a special USB dongle. This has a 900 MHz radio which picks out the packets from a reasonably large list of meter types, and pushes them through the USB interface. In the image above you can see that an Arduino with a USB host shield is used, but there are also drivers if you want to connect this directly to your computer.
We looked around and didn’t find any specifics on the hardware used on that board. But it can’t be all that hard to make one of these at home… the populated board seems to have just two ICs and a few passive components. Anyone up to the challenge of hacking together their own packet sniffer? We wonder if the Next HOPE badge could pull down the data?
[Thanks Chris]