If you’ve been trying to think of stuff you can do with the DCPU-16 this may inspire you to write a clone of a classic game.
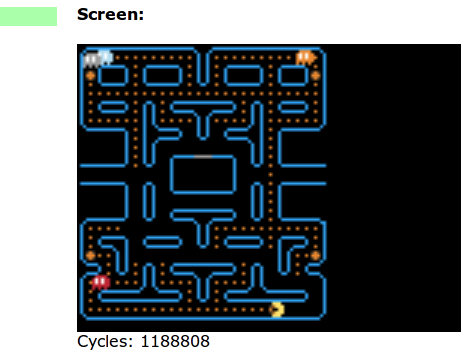
This version of Pac-Man was written using a sprite system with a 16 color pallette. It runs in an HTML-based emulator, so you can even monkey around with the assembly code to help you figure out how it works. But if you’re not into writing code that is this machine-close, you can just click the ‘run’ button and use your keyboard arrows to play through a level or two. You’ll notice there’s only one game board available so far and some things are still missing like that familiar waka-waka as he gobbles up the dots. Let us know if you mange to extend the features of this version.
In case you missed it, this emulator is running the DCPU-16 spec from Notch’s new game, 0x10c (. We have no idea how that’s going to shape up, but getting in on the game early will pay off it turns out to be as popular as Minecraft.