In a few weeks the Hackaday community offline password keeper will reach a crowdfunding platform. This is a necessary step as only a high production volume will allow our $80 early bird perk target. We’ll therefore need you to spread the word.
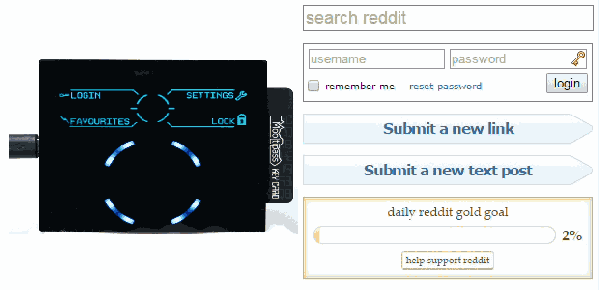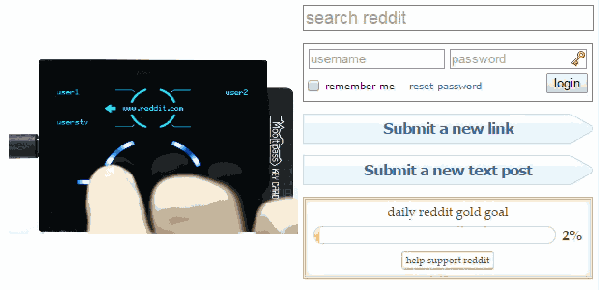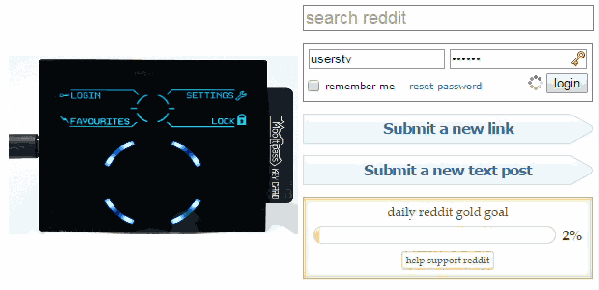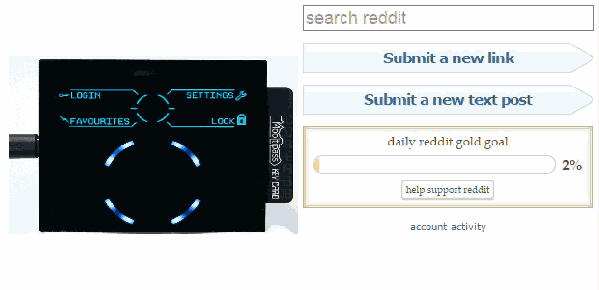
Thanks to the Chromium development team, a few days ago the Mooltipass installation process became as simple as installing our app & extension. As you may remember, our device is enumerated as composite HID proprietary / HID standard keyboard. This makes it completely driverless for all operating systems and enables standalone operation as the Mooltipass can type logins and passwords selected through its user interface. Management communications are therefore done through the Mooltipass HID proprietary interface, which Chrome 38 now natively supports through its chrome.hid API. The simpler our installation process is, the more likely the final users will appreciate the fruit of our hard labor.
As our last post mentioned there’s still plenty of space for future contributors to implement new functionalities. Our future crowdfunding campaign will allow us to find javascript developers for the remaining app & extensions tasks and also implement other browsers support. Want to stay tuned of the Mooltipass launch date? Subscribe to our official Google Group!