Good news, bad news for Sun watchers this week, as our star launched a solar flare even bigger than the one back in May that gave us an amazing display of aurora that dipped down into pretty low latitudes. This was a big one; where the earlier outburst was only an X8.9 class, the one on July 23 was X14. That sure sounds powerful, but to put some numbers to it, the lower end of the X-class exceeds 10-4 W/m2 of soft X-rays. Numbers within the class designate a linear increase in power, so X2 is twice as powerful as X1. That means the recent X14 flare was about five times as powerful as the May flare that put on such a nice show for us. Of course, this all pales in comparison to the strongest flare of all time, a 2003 whopper that pegged the needle on satellite sensors at X17 but was later estimated at X45.
sabotage3 Articles
A Daring Search For Answers In Soyuz Mystery
If you happened to tune into NASA TV on December 11th, you’d have been treated to a sight perhaps best described as “unprecedented”: Russian cosmonauts roughly cutting away the thermal insulation of a docked Soyuz spacecraft with a knife and makeshift pair of shears. Working in a cloud of material ripped loose during the highly unusual procedure, cosmonauts Oleg Kononenko and Sergey Prokopyev were effectively carving out their own unique place in space history. Their mission was to investigate the external side of the suspicious hole in the Soyuz MS-09 capsule which caused a loss of air pressure on the International Space Station earlier in the year.
 That astronauts don’t generally climb out the hatch and use a knife to hack away at the outside of their spacecraft probably goes without saying. Such an event has never happened before, and while nobody can predict the future, odds are it’s not something we’re likely to see again. Keep in mind that this wasn’t some test capsule or a derelict, but a vehicle slated to return three human occupants to Earth in a matter of days. Cutting open a spacecraft in which human lives will shortly be entrusted is not a risk taken likely, and shows how truly desperate the Russian space agency Roscosmos is to find out just who or what put a hole in the side of one of their spacecraft.
That astronauts don’t generally climb out the hatch and use a knife to hack away at the outside of their spacecraft probably goes without saying. Such an event has never happened before, and while nobody can predict the future, odds are it’s not something we’re likely to see again. Keep in mind that this wasn’t some test capsule or a derelict, but a vehicle slated to return three human occupants to Earth in a matter of days. Cutting open a spacecraft in which human lives will shortly be entrusted is not a risk taken likely, and shows how truly desperate the Russian space agency Roscosmos is to find out just who or what put a hole in the side of one of their spacecraft.
Close inspection from the inside of the spacecraft confirmed the hole wasn’t made by an impact with a micrometeorite or tiny piece of space junk as was originally assumed. It appears to have been made with a drill, which really only allows for two possible scenarios: intentional sabotage or a mistake and subsequent cover-up. In either event, a truly heinous crime has been committed and those responsible must be found. As luck would have it the slow leak of air pressure was detected early and the hole was patched before any damage was done, but what if it hadn’t?
Continue reading “A Daring Search For Answers In Soyuz Mystery”
Industrial Robots, Hacking And Sabotage
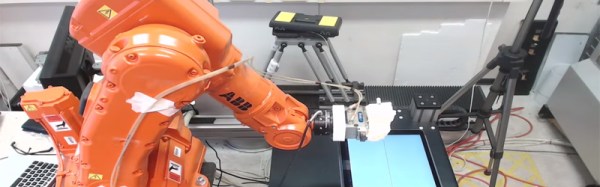
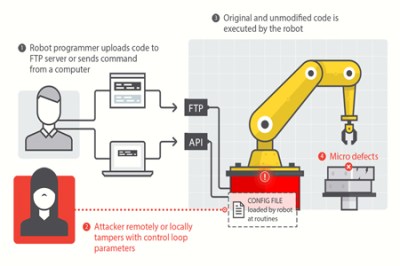
Everything is online these days creating the perfect storm for cyber shenanigans. Sadly, even industrial robotic equipment is easily compromised because of our ever increasingly connected world. A new report by Trend Micro shows a set of attacks on robot arms and other industrial automation hardware.
This may not seem like a big deal but image a scenario where an attacker intentionally builds invisible defects into thousands of cars without the manufacturer even knowing. Just about everything in a car these days is built using robotic arms. The Chassis could be built too weak, the engine could be built with weaknesses that will fail far before the expected lifespan. Even your brake disks could have manufacturing defects introduced by a computer hacker causing them to shatter under heavy braking. The Forward-looking Threat Research (FTR) team decided to check the feasibility of such attacks and what they found was shocking. Tests were performed in a laboratory with a real in work robot. They managed to come up with five different attack methods.
Why are these robots even connected? As automated factories become more complex it becomes a much larger task to maintain all of the systems. The industry is moving toward more connectivity to monitor the performance of all machines on the factory floor, tracking their service lifetime and alerting when preventive maintenance is necessary. This sounds great for its intended use, but as with all connected devices there are vulnerabilities introduced because of this connectivity. This becomes especially concerning when you consider the reality that often equipment that goes into service simply doesn’t get crucial security updates for any number of reasons (ignorance, constant use, etc.).
For the rest of the attack vectors and more detailed info you should refer to the report (PDF) which is quite an interesting read. The video below also shows insight into how these type of attacks might affect the manufacturing process.