In just a few days time, Google’s Stadia game streaming service will finally shut down for good. But not for any technical reason, mind you. Microsoft has managed to demonstrate that streaming modern games over home and even mobile Internet connections is viable with their immensely popular Game Pass Ultimate service, and NVIDIA is making similar inroads with GeForce Now. No, like so many of Google’s failed experiments, they’ve simply decided they don’t want to play anymore and are taking their proverbial ball home back with them.
But not all is lost for those who shelled out money for Stadia’s wares. Not only will Google be refunding any money players spent on games, but a company representative has also announced they will be releasing a tool to unlock the latent Bluetooth capabilities of the service’s custom controller — hopefully stemming a surge of e-waste before it starts.
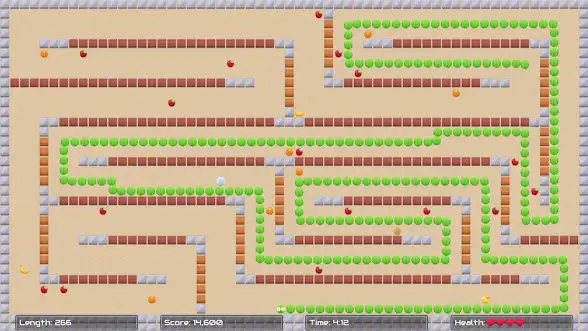
In a forum thread titled “A Gift from the Stadia Team”, Community Manager [DanFromGoogle] explains that information on how you can enable Bluetooth on the controller will be coming next week. In the meantime, he also announced the immediate release of “Worm Game”, a tech demo that staffers apparently used to test out capabilities of the streaming service before its public release.
That this ridiculously simple game, which looks all the world like something a kid would crank out during an after-school programming class, will be the final title to officially release on Stadia is a stunningly insulting epitaph for the fledgling service. But then, Google seems to have developed a special affinity for mistreating their most loyal cattle users over these last few years.
Enabling Bluetooth on a game controller might not seem like such a big deal, but in this case, it will potentially give the piece of hardware a second chance at life. The Stadia controller is unique in that it uses WiFi to communicate directly over the Internet to Google’s streaming service, so once those servers stop responding, the orphaned device will end up being little more than a curiosity. Although it does technically work over USB, being able to use it wirelessly will not only provide a more modern experience, but help justify its internal batteries.
The last time we mentioned the Stadia controller, it was to document one user’s attempt to rid it of an internal microphone they didn’t feel comfortable with. Now that the service is being put to pasture, we wonder if we’ll start to see more hacks involving the admittedly interesting peripheral. We’ll certainly be keeping an eye out for them, but if you see anything we miss, you know where to send it.