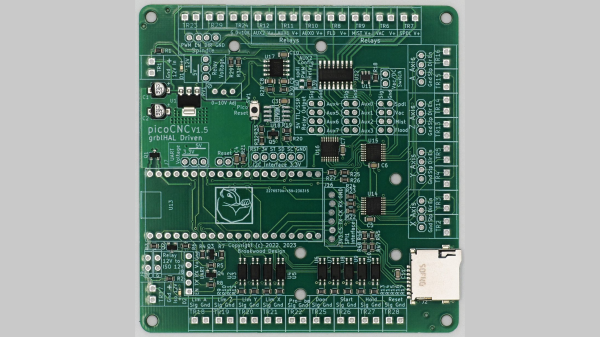
[Phil Barrett] designed a new CNC controller breakout board called the PicoCNC which uses the Raspberry Pi Pico RP2040 module and grblHAL. It packs a bunch of features typical of these controllers, and if you use the Pico W, you get WiFi connectivity along with USB. And if you don’t want connectivity, you can execute G-code directly from a micro SD card. The board is available in kit form, and schematics are posted on the GitHub repository above. Some of the features include four axes of motion, spindle control, limit switches, relay drivers, expansion headers, and opto-isolation.
This isn’t [Phil]’s first controller board. He also designed the grblHAL-based Teensy CNC controller breakout board, a step up from the usual Arduino-based modules at the time and boasting Ethernet support as well. According to the grblHAL site, nine different processors are now supported. There are well over a dozen CNC controller breakout boards listed as well. And don’t forget [bdring]’s 6-Pack grbl-ESP32 controller, a modular breakout board we covered a few years back. So pick your favorite board or roll your own and get moving.