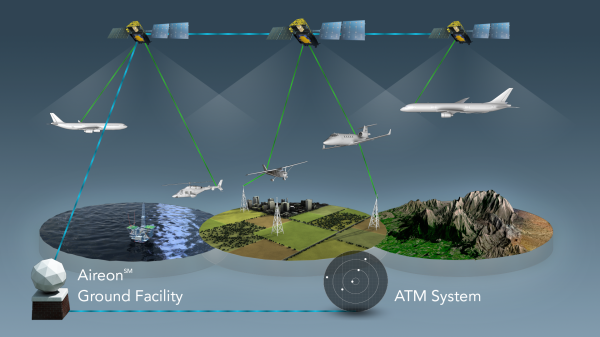
SpaceX just concluded 2017 by launching 10 Iridium NEXT satellites. A footnote on the launch was the “hosted payload” on board each of the satellites: a small box of equipment from Aireon. They will track every aircraft around the world in real-time, something that has been technically possible but nobody claimed they could do it economically until now.
Challenge one: avoid adding cost to aircraft. Instead of using expensive satcom or adding dedicated gear, Aireon listen to ADS-B equipment already installed as part of international air traffic control modernization. But since ADS-B was designed for aircraft-to-aircraft and aircraft-to-ground, Aireon had some challenges to overcome. Like the fact ADS-B antenna is commonly mounted on the belly of an aircraft blocking direct path to satellite.
Challenge two: hear ADS-B everywhere and do it for less. Today we can track aircraft when they are flying over land, but out in the middle of the ocean, there are no receivers in range except possibly other aircraft. Aireon needed a lot of low-orbit satellites to ensure you are in range no matter where you are. Piggybacking on Iridium gives them coverage at a fraction of the cost of building their own satellites.
Continue reading “Aireon Hitchhikes On Iridium To Track Airplanes”





![[M0CVO]'s Tweet that started it all](https://hackaday.com/wp-content/uploads/2017/10/screenshot-2017-10-31-nigel-booth-on-twitter.png?w=298)









