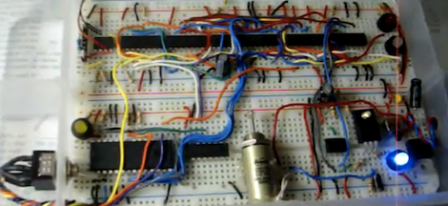
[Eric] needed a project for his digital logic design class, and decided on a lock that open in response to a specific pattern of knocks. This is a fairly common project that we’ve seen a few builds with ‘knock locks,’ but this one doesn’t use a microcontroller. Instead, it uses individual logic chips.
The lock senses the knocks with a piezo, just like every other build we’ve seen. Unlike the other builds, the knock pattern is then digitized and stored in an EEPROM. [Eric] only used 12 chip for this build, a feat he could accomplish with a few digital tricks, like making an inverter by tying one XOR input high.
We’ve seen a 555-based knock lock before, but getting the timing right with that seems a little maddening. [Eric]’s build seems much more user-friendly, and has the added bonus of being programmed by knocking instead of turning potentiometers. Check out [Eric]’s knock lock after the break.