
Popular Mechanics has an interview with [Zach Anderson], one of the MIT hackers that was temporarily gagged by the MBTA. The interview is essentially a timeline of the events that led up to the Defcon talk cancellation. [Zach] pointed out a great article by The Tech that covers the vulnerabilities. The mag stripe cards can be easily cloned. The students we’re also able to increase the value of the card by brute forcing the checksum. There are only 64 possible checksum values, so they made a card for each one. It’s not graceful, but it works. The card values aren’t encrypted and there isn’t an auditing system to check what values should be on the card either. The RFID cards use Mifare classic, which we know is broken. It was NXP, Mifare’s manufacturer, that tipped off the MBTA on the actual presentation.
Security Hacks1541 Articles
Red Hat Confirms Security Breach

After a week of wondering, Red Hat has confirmed that someone broke in and compromised their security. Although It doesn’t appear the attacker was able to retrieve the passphrase used to sign Fedora packages, the team is switching to new keys. In a separate intrusion the attacker tampered with and signed OpenSSH packages for RHEL. While it’s good to get the full story, no one is happy how long it took Red Hat to release these details.
[via Zero Day]
[photo: afsilva]
The Underhanded Hardware Challenge
The Polytechnic Institute of NYU is hosting an interesting embedded systems contest. They’ve constructed a solid state cryptographic device that uses a 128-bit private key. Contestants will be tasked with designing and implementing several trojans into the system that will undermine the security. The system is built on a Digilent BASYS Spartan-3 FPGA board. The trojans could do a wide variety of things: transmitting unencrypted, storing and transmitting previously entered plain text, or just shutting down the system entirely. The modified devices still need to pass the factory testing procedure though, which will measure power consumption, code size, and function. After a qualification round, participants will be given the necessary hardware to compete.
[via NYC Resistor (Happy Birthday!)]
How To Hotwire Your Own Car

Picture this scenario: it’s 2 AM, you’re stuck somewhere you’d rather not be, and you’ve lost your car keys. If you can’t call the Auto Club, what do you do? Hotwire your own car, of course. Wired.com has a wiki article detailing all the things you need to do to get that car running: how to identify which wires to connect, potential pitfalls of newer cars that require an RFID chip in the key, and so on. Of course, hotwiring a car that doesn’t belong to you is illegal, but this is one of those skills-like lockpicking-which just might come in handy in an emergency.
[Photo: D.B. Blas]
Antivirus Products Still Fail On Fresh Viruses
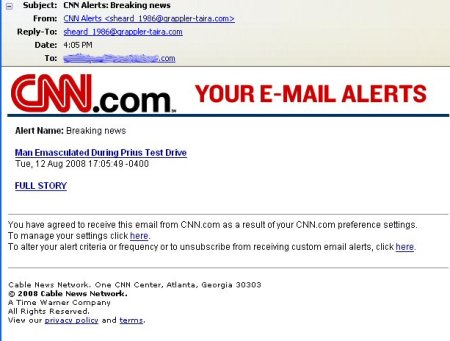
Many computer users rely on antivirus software from McAfee and Symantec to protect their computers from malware, worms, and viruses. Since the creation of viruses outpaces the protection abilities of the software, antivirus protection lags behind and may not be as secure as you think. [Gary Warner] provides some examples of current malware making the rounds that continue to be unaddressed by anti-virus vendors, including the recent “CNN Alerts: Breaking News” spam, which morphed into MSNBC alert spoofs. Our advice? Keep your antivirus software updated, but don’t believe that it will catch everything for you. Only open files from sources you know and trust.
[via Waxy]
Criminals Steal Credit Card Data Just By Wardriving

A federal grand jury in Boston has charged eleven people with the theft of more than 41 million credit and debit card numbers from retail stores. What makes this case interesting is that, although the defendants stole the data from retail establishments, they did so without ever having to leave their cars; they stole the numbers while wardriving. While the report doesn’t make it clear whether the targeted networks used weak encryption or were simply unsecured, it’s obvious that the security of your data is still not a top priority for many companies.
[photo: Mujitra]
Biometric Locks Turned Trojan

In the same vein as our recent Defcon article on biometric cloning, White Wolf Security has released this article about turning a biometric door lock into a trojan. They note that there are many common ways to break into one, from harvesting fingerprints to using gummy bears to fake a finger. This hack involves having full access to the unit so you can disassemble it.
The unit has a system built-in where you can touch a 9-volt battery to some connectors on the bottom to power it in case of a building power failure. The researchers simply routed some wires from the motorized lock to the plates used for the 9-volt and then reassembled the lock. The door can then be opened at any time without verification, even if the software on the unit is reset.
[Thanks, dwight]










