The NeXT slabs and cubes were interesting computers for their time, with new interesting applications that are commonplace today seen first in this block of black plastic. Web browsers, for example, were first seen on the NeXT.
Running one of these machines today isn’t exactly easy; there are odd video connectors but you can modify some of the parts and stick them in an LCD monitor. It’s a tradeoff between a big, classic, heavy but contemporary CRT and a modern, light, and efficient LCD, but it’s still a great way to get a cube or slab up and running if you don’t have the huge monitor handy.
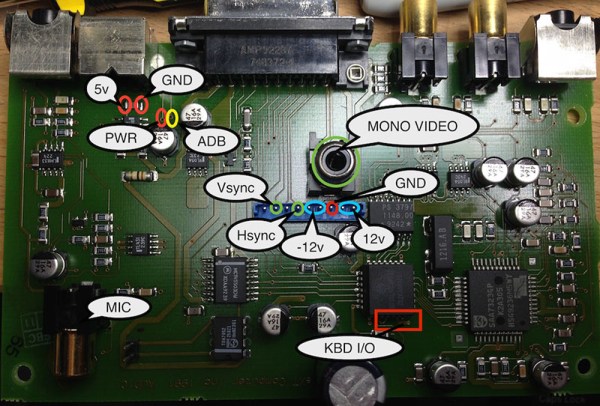
The NeXT cube doesn’t have a single wire going between the computer and the monitor; that would be far too simple. Instead, a NeXT Sound Box sits between the two, providing the user a place to plug the monitor, keyboard, mouse, and audio connectors into. [Brian] took the board from this Sound Box and put it inside an old NEC LCD monitor he had sitting around. 12V and 5V rails were wired in, the video lines were wired in, and [Brian] created a new NeXT monitor.
There are two versions of the NeXT Sound Box – one for ADB peripherals (Apple IIgs and beige Macs), and another for non-ADB peripherals. [Brian] also put together a tutorial for using non-ADB peripherals with the much more common ADB Sound Board.