If you’re an Evil Customs Agent or other nefarious Three Letter Agency Person, you’re probably very interesting in getting data off people’s phones. Even if the screen is locked, there’s a way around this problem: just use the Android Debug Bridge (ADB), a handy way to get a shell on any Android device with just a USB cable. The ADB can be turned off, though, so what is the Stasi to do if they can’t access your phone over ADB? [Michael Ossmann] and [Kyle Osborn] have the answer that involves a little-known property of USB devices.
USB mini and micro plugs have five pins – power, ground, D+, D-, and an oft-overlooked ID pin. With a particular resistance between this ID pin and ground, the USB multiplexor inside your phone can allow anyone with the proper hardware to access the state of the charger, get an audio signal, mess around with the MP3s on your device, or even get a shell.
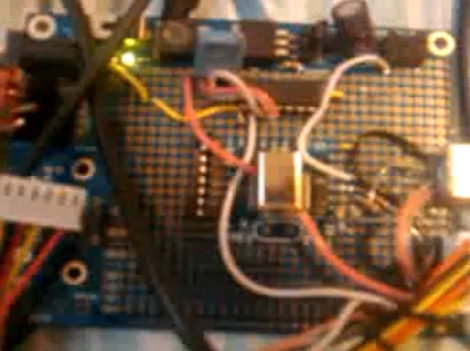
To test their theory, [Michael] and [Kyle] rigged up a simple USB plug to UART adapter (seen above) that included a specific value of resistor to enable a shell on their test phone. Amazingly, it worked and the thought of having a secure phone was never had again.
The guys went farther with some proprietary Samsung hardware that could, if they had the service manual, unlock any samsung phone made in the last 15 years. They’re working on building a device that will automagically get a shell on any phone and have built some rather interesting hardware. If you’re interested in helping them out with their project, they have a project site up with all the information to get up to speed on this very ingenious hack.