[Reinis] has a Volvo S80. One of the dashboard features it includes is a 6.5″ LCD screen which periscopes up to use as a navigation system. The problem is that Volvo stopped making maps for it around five years ago and there are no maps at all for Latvia where he lives. So it’s worthless… to you’re average driver. But [Reinis] is fixing it on his own by replacing the system with a Raspberry Pi.
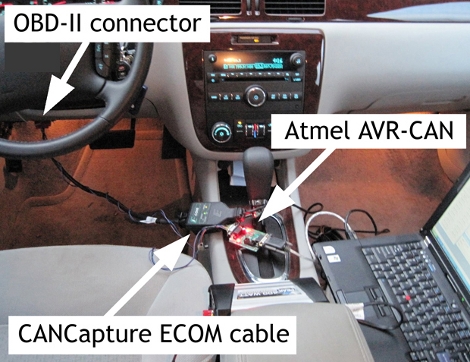
That link leads to his project overview page. But he’s already posted follow-ups on hardware design and initial testing. He’s basing the design around a Raspberry Pi board, but that doesn’t have all the hardware it needs to communicate with the car’s systems. For this he designed his own shield that uses an ATmega328 along with a CAN controller and CAN transceiver. The latter two chips patch into the CAN bus on the car’s On Board Diagnostic system. We didn’t see much about the wiring, but the overview post mentions that the screen takes RGB or Composite inputs so he must be running a composite video cable from the trunk to the dashboard.