In the old days, spies eavesdropped on each other using analog radio bugs. These days, everything’s in the cloud. [Sebastian] from [Hacking Beaver] wondered if he could make a WiFi bug that was small and cheap besides. Enter the ESP8266 and some programming wizardry.
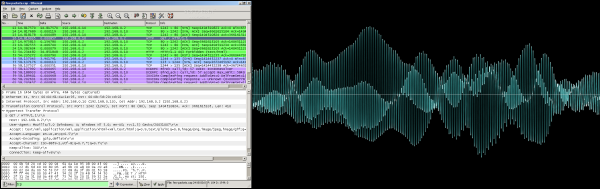
[Sebastian] is using a NodeMCU but suggests that it could be pared down to any ESP8266 board — with similar cuts made to the rest of the electronics — but has this working as a proof of concept. A PIC 18 MCU samples the audio data from a microphone at 10 kHz with an 8-bit resolution, dumping it into a 512-byte buffer. Once that fills, a GPIO pin is pulled down and the ESP8266 sends the data to a waiting TCP server over the WiFi which either records or plays the audio in real-time.
[Sebastian] has calculated that he needs at least 51.2 ms to transfer the data which this setup easily handles, but there are occasional two to three second glitches that come out of the blue. To address this and other hangups, [Sebastian] has the ESP8266 control the PIC’s reset pin so that the two are always in sync.