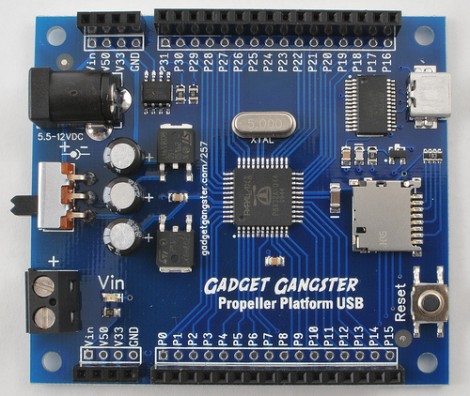
[Nick] over at Gadget Gangster has a new version of his prototyping hardware for Propeller microcontrollers, called the Propeller Platform USB. A little more than a year ago we looked at the last version which was larger, used a DIP processor, and came unassembled. The new version does come assembled because of the migration to surface mount components (which may take some of the fun out of it if you just love soldering kits). This not only reduces the board footprint, but makes room for more goodies. As the name implies, there’s now a mini-USB socket with a USB to UART bridge, a microSD card slot as been added, and the onboard EEPROM has been doubled. This is a nice hardware upgrade but the price has been upgraded by $25 as well. No worries, it’s open source so you can roll your own if you have the parts on hand.

 A
A











