Get your feet wet with Time-based One-Time Password (TOTP) security by building your own Arduino OATH system. OATH is an open standard authentication system that provides a platform to generate tokens, making your login more secure than a password alone would.
The TOTP approach is what is used with many companies that issue hardware-based dongles for logging in remotely. This security may have been compromised but it’s still better than passwords alone. Plus, if you’re building it around an Arduino we’d bet you’re just trying to learn and not actually responsible for protecting industrial or state secrets.
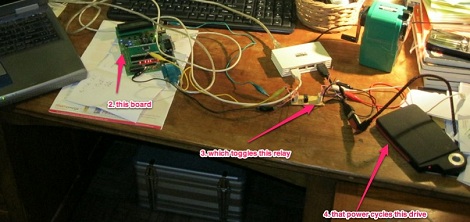
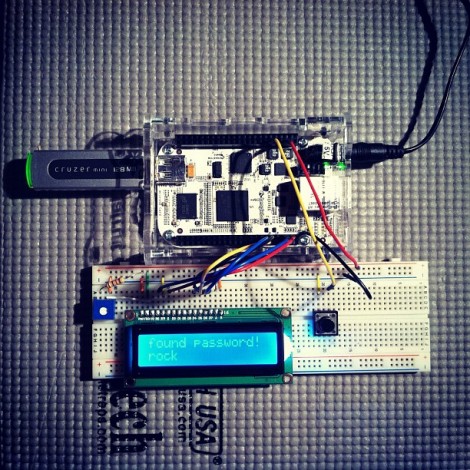
The hardware setup requires nothing more than the Arduino board with one button and a screen as a user interface. Since the board has a crystal oscillator it keeps fairly accurate time (as long as it remains powered). It will push out a new token every thirty seconds. The video after the break shows that the Arduino-calculated value does indeed match what the test box is displaying.
Continue reading “Time-based One-Time Passwords With An Arduino”