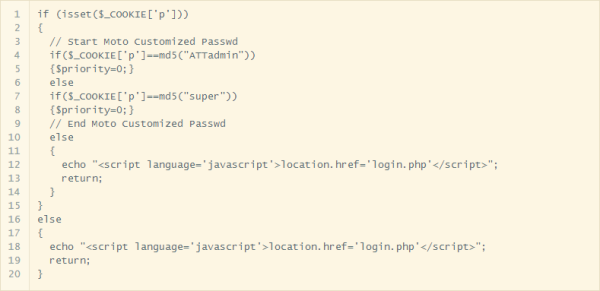
The big story of the last week is a problem in F5’s BIG-IP devices. A rather trivial path traversal vulnerability allows an unauthenticated user to call endpoints that are intended to be restricted to authenticated. That attack can apparently be as simple as:
'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin'
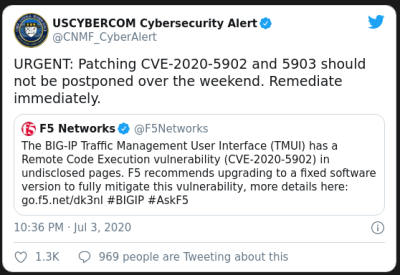 A full exploit has been added to the metasploit framework. The timeline on this bug is frighteningly quick, as it’s apparently being actively exploited in the wild. F5 devices are used all over the world, and this vulnerability requires no special configuration, just access to the opened management port. Thankfully F5 devices don’t expose the vulnerable interface to the internet by default, but there are still plenty of ways this can be a problem.
A full exploit has been added to the metasploit framework. The timeline on this bug is frighteningly quick, as it’s apparently being actively exploited in the wild. F5 devices are used all over the world, and this vulnerability requires no special configuration, just access to the opened management port. Thankfully F5 devices don’t expose the vulnerable interface to the internet by default, but there are still plenty of ways this can be a problem.
Freta
Microsoft has made a new tool publicly available, Freta. This tool searches for rootkits in uploaded memory snapshots from a Linux VM. The name, appropriately, is taken from the street where Marie Curie was born.
The project’s namesake, Warsaw’s Freta Street, was the birthplace of Marie Curie, a pioneer of battlefield imaging.
The impetus behind the project is the realization that once a malicious actor has compromised a machine, it’s possible to compromise any security software running on that machine. If, instead, one could perform a security x-ray of sorts, then a more reliable conclusion could be reached. Freta takes advantage of the VM model, and the snapshot capability built into modern hypervisors.
Continue reading “This Week In Security: F5, Novel Ransomware, Freta, And Database Woes”