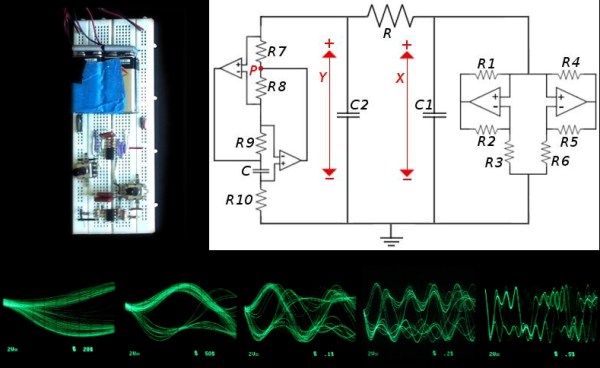
Chua’s circuit is the simplest electronic circuit that produces chaos—the output of this circuit never repeats the same sequence, and is a truly random signal. If you need a good source of randomness, Chua’s circuit is easy to make and is built around standard components that you might have lying around. [Valentine] wrote a comprehensive guide which walks you through the process of building your own source of chaos.
The chaos of Chua’s circuit is derived from several elements, most importantly a nonlinear negative resistor. Unfortunately for us, this type of resistor doesn’t exist in a discrete form, so we have to model it with several other components. This resistor, also known as Chua’s diode, can be created with an op-amp configured as a negative impedance converter and a couple pairs of diodes and resistors. Other variations such, as the schematic above,22`01 model Chua’s diode using only op-amps and resistors.
The rest of the circuit is quite simple: only two capacitors, an inductor, and a resistor are needed. [Valentine] does note that the circuit is quite sensitive, so you might encounter issues when building it on a breadboard. The circuit is very sensitive to vibration (especially on a breadboard), and good solder connections are essential to a reliable circuit. Be sure to check out the Wikipedia article on Chua’s circuit for a brief overview of the circuit’s functionality and a rabbit trail of information on chaos theory.