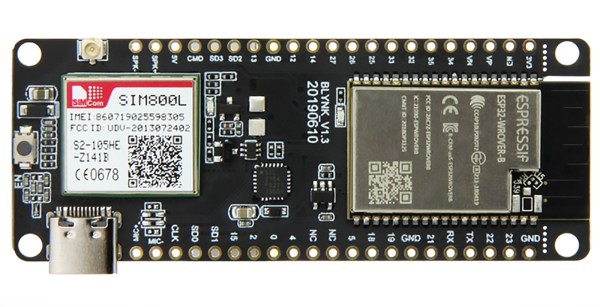
Cruise around AliExpress for long enough and you’ll find some interesting new hardware. The latest is the TTGO T-Call, an ESP32 breakout board that also has a cellular modem. Yes, it’s only a 2G modem, but that still works in a lot of places, and the whole thing is $15.
On board the TTGO T-Cal is the ESP-WROVER-B, the same module you all know and love that features a dual-core ESP running at 240 MHz with 4 MB of Flash and 8 MB of SRAM. Add to this WiFi and Bluetooth, and you have a capable microcontroller platform. Of note is that this board includes a USB-C port, ostensibly wired so that it behaves like a normal USB micro port. That’s neat, 2019 is the year USB C connectors became cheaper than USB micro connectors.
In addition to the ESP32 module, there’s also cellular in the form of a SIM800 module. This module has been around for a while and used in many, many cellular-connected projects and products like the ZeroPhone. This module is only a 2G module, and that’ll be going away shortly (if not already) in built-up areas, but this can serve as a building block for modules that have more Gees than a 2G module. That said, if you’re looking for a WiFi and cellular bridge for fifteen bucks, you could do a lot worse for a lot more money.