GPS can be a bit complex of a technology – you have to receive a signal below the noise floor, do quite a bit of math that relies on the theory of relativity, and, adding insult to injury, you also have to go outside to test it. Have you ever wondered how GPS antennas work? In particular, how do active GPS antennas get power down the same wire that they use to send signal to the receiver? Wonder not, because [Tom Verbeure] gifts us a post detailing a mod letting a fancy active GPS antenna use a higher-than-expected input voltage.
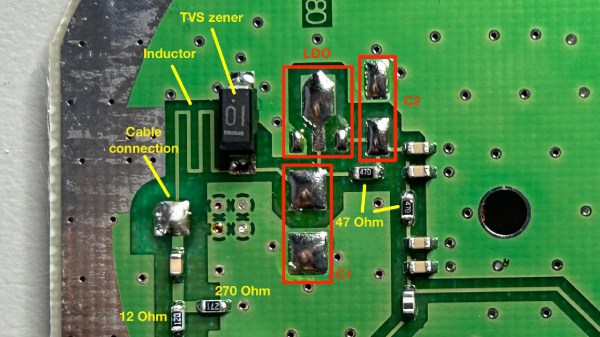
[Tom]’s post has the perfect amount of detail – enough pictures to illustrate the entire journey, and explanations to go with all of it. The specific task is modifying a Symmetricom antenna to work with a Symmetricom GPS receiver, which has a puzzling attribute of supplying 12V to the antenna instead of more common 3.3V or 5V. There’s a few possible options detailed, and [Tom] goes for the cleanest possible one – replacing the voltage regulator used inside of the antenna.
With a suitable replacement regulator installed and a protection diode replaced, the antenna no longer registers as a short circuit, and gets [Tom] a fix – you, in turn, get a stellar primer on how exactly active GPS antennas work. If your device isn’t ready to use active GPS antennas, [Tom]’s post will help you understand another GPS antenna hack we covered recently – modifying the Starlink dish to use an active antenna to avoid jamming on the frontlines.