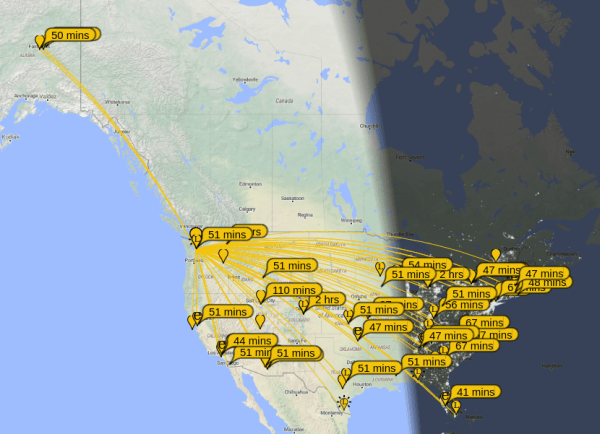
While most of us carry cell phones that have GPS and other location services, they require a significant amount of infrastructure to be useful. Drive from Washington to Alaska like [Lonney] did a while back, where that infrastructure is essentially nonexistent, and you’ll need to come up with some other solutions to let friends and family know where you are.
A tool called the Automatic Packet Reporting System (APRS) is fairly robust in the very high frequency (VHF) part of the amateur radio spectrum, but this solution still relies on a not-insignificant amount of infrastructure for the limited distances involved with VHF. [Lonney] adapted a few other tools to get APRS up and running in the HF range, letting his friends keep tabs on him even from the most remote locations.
Continue reading “Automatic Position Reporting Over HF Radio”






 The build is based around a PCB and 3D-printed components that roughly ape the design of a cassette tape. It even replicates the typical center window of a cassette tape by using a transparent OLED screen, which displays the user interface. In a neat way, the graphics on the display are designed to line up with those on the PCB, which looks excellent.
The build is based around a PCB and 3D-printed components that roughly ape the design of a cassette tape. It even replicates the typical center window of a cassette tape by using a transparent OLED screen, which displays the user interface. In a neat way, the graphics on the display are designed to line up with those on the PCB, which looks excellent.










