The dystopian future you’ve been expecting is here now, at least if you live in New York City, which unveiled a trio of technology solutions to the city’s crime woes this week. Surprisingly, the least terrifying one is “DigiDog,” which seems to be more or less an off-the-shelf Spot robot from Boston Dynamics. DigiDog’s job is to de-escalate hostage negotiation situations, and unarmed though it may be, we suspect that the mission will fail spectacularly if either the hostage or hostage-taker has seen Black Mirror. Also likely to terrify the public is the totally-not-a-Dalek-looking K5 Autonomous Security Robot, which is apparently already wandering around Times Square using AI and other buzzwords to snitch on people. And finally, there’s StarChase, which is based on an AR-15 lower receiver and shoots GPS trackers that stick to cars so they can be tracked remotely. We’re not sure about that last one either; besides the fact that it looks like a grenade launcher, the GPS tracker isn’t exactly covert. Plus it’s only attached with adhesive, so it seems easy enough to pop it off the target vehicle and throw it in a sewer, or even attach it to another car.
uber15 Articles
This Week In Security: Malwarebytes Goes Nuts, Uber
I got a rude awakening Wednesday morning this week. HaD writers don’t necessarily keep normal hours — don’t judge. A local client called, complaining that Google Maps was blocking on one of their computers, and the browser stated that it was a malicious site. Well that got my attention. Standard incident response: “Turn off the affected computers, I’m on my way.” Turns out, it was Malwarebytes that was complaining and blocking Google Maps, as well as multiple other Google domains. That particular machine happened to have a fresh install of the program, and was still in the trial period of Malwarebytes premium, which includes the malicious IP and domain blocking feature.
Oof, this could be bad. The first possibility that came to mind was a DNS hijack. The desktop’s DNS was set to the router, and the router’s DNS was set to the ISP’s. Maybe the ISP had their DNS servers compromised? Out came the cell phone, disconnected from the WiFi, for DNS lookups on some Google domains. Because Google operates at such a massive scale, they have multiple IPs serving each domain, but since the two different results were coming from the same subnet, the suspicious DNS server was likely OK. A whois on the blocked IP also confirmed that it was a Google-owned address. We were running out of explanations, and as a certain fictional detective was known for saying, “whatever remains, however improbable, must be the truth.” And, yes, Malwarebytes did indeed accidentally add Google to its bad list. The upside was that my customer wasn’t compromised. The downside? I had to answer a phone call before my first cup of coffee. Blegh.
Continue reading “This Week In Security: Malwarebytes Goes Nuts, Uber”
Uber Traded Away Its In-House Self-Driving Effort
Perhaps the best-known ridesharing service, Uber has grown rapidly over the last decade. Since its founding in 2009, it has expanded into markets around the globe, and entered the world of food delivery and even helicopter transport.
One of the main headline research areas for the company was the development of autonomous cars, which would revolutionize the company’s business model by eliminating the need to pay human drivers. However, as of December, the company has announced that it it spinning off its driverless car division in a deal reportedly worth $4 billion, though that’s all on paper — Uber is trading its autonomous driving division, and a promise to invest a further $400 million, in return for a 26% share in the self-driving tech company Aurora Innovation.
Playing A Long Game

Uber’s driverless car research was handled by the internal Advanced Technologies Group, made up of 1,200 employees dedicated to working on the new technology. The push to eliminate human drivers from the ride-sharing business model was a major consideration for investors of Uber’s Initial Public Offering on the NYSE in 2019. The company is yet to post a profit, and reducing the amount of fares going to human drivers would make it much easier for the company to achieve that crucial goal.
However, Uber’s efforts have not been without incident. Tragically, in 2018, a development vehicle running in autonomous mode hit and killed a pedestrian in Tempe, Arizona. This marked the first pedestrian fatality caused by an autonomous car, and led to the suspension of on-road testing by the company. The incident revealed shortcomings in the company’s technology and processes, and was a black mark on the company moving forward.
The Advanced Technology Group (ATG) has been purchased by a Mountain View startup by the name of Aurora Innovation, Inc. The company counts several self-driving luminaries amongst its cofounders. Chris Urmson, now CEO, was a technical leader during his time at Google’s self-driving research group. Drew Bagnell worked on autonomous driving at Uber, and Sterling Anderson came to the startup from Tesla’s Autopilot program. The company was founded in 2017, and counts Hyundai and Amazon among its venture capital investors.
Aurora could also have links with Toyota, which also invested in ATG under Uber’s ownership in 2019. Unlike Uber, which solely focused on building viable robotaxis for use in limited geographical locations, the Aurora Driver, the core of the company’s technology, aims to be adaptable to everything from “passenger sedans to class-8 trucks”.
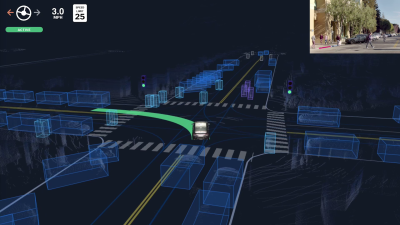
Getting rid of ATG certainly spells the end of Uber’s in-house autonomous driving effort, but it doesn’t mean they’re getting out of the game. Holding a stake in Aurora, Uber still stands to profit from early investment, and will retain access to the technology as it develops. At the same time, trading ATG off to an outside firm puts daylight between the rideshare company and any negative press from future testing incidents.
Even if Aurora only retains 75% of ATG’s 1,200 employees, it’s doubling in size, and will be worth keeping an eye on in the future.
Ludwig Promises Easy Machine Learning From Uber
Machine learning has brought an old idea — neural networks — to bear on a range of previously difficult problems such as handwriting and speech recognition. Better software and hardware has made it feasible to apply sophisticated machine learning algorithms that would have previously been only possible on giant supercomputers. However, there’s still a learning curve for developing both models and software to use these trained models. Uber — you know, the guys that drive you home when you’ve had a bit too much — have what they are calling a “code-free deep learning toolbox” named Ludwig. The promise is you can create, train, and use models to extract features from data without writing any code. You can find the project itself on GitHub.io.
The toolbox is built over TensorFlow and they claim:
Ludwig is unique in its ability to help make deep learning easier to understand for non-experts and enable faster model improvement iteration cycles for experienced machine learning developers and researchers alike. By using Ludwig, experts and researchers can simplify the prototyping process and streamline data processing so that they can focus on developing deep learning architectures rather than data wrangling.
Continue reading “Ludwig Promises Easy Machine Learning From Uber”
Hackaday Links: CES Is Over
CES is over, and once again we have proof technology does not improve our lives. Here’s the takeaway from the @internetofshit. There’s a garbage can where you can drop your DNA sample. This is obviously not a Bay Area startup, because they just leave DNA samples on the sidewalk there. The ‘smart cooler’ market is heating up (literally) with a cooler that’s also a grill. Someone duct taped an air filter to a roomba, so your air filter can go to where all the dirty air is in your house. Internet of Rubik’s Cubes. The world’s first autonomous shower made an appearance. Now you can take a shower over the Internet. What a time to be alive.
Need some more bad news from CES? We have more proof the entire tech industry is astonishingly sexist. How so? Well, VR sex simulators can win best of show. That’s a given, obviously. But a ‘smart’ sex toy designed by and for women was selected for a CES 2019 Innovation Award in the Robotics and Drone category. This award was given, then rescinded, by the Consumer Technology Association (CTA) because it was, ‘immoral, obscene, indecent, profane or not in keeping with the CTA’s image’. We presume they mean the latter, but we’re not sure.
Sometimes, though, there are actual engineers behind some of the gadgets on display at CES. Bell (yes, the aerospace company) unveiled the Bell Nexus, a five-seat VTOL ‘taxi’ powered by six ducted fans. These fans are powered by a hybrid electric power system. We assume a turboshaft connected to a generator powering electric motors. Most interestingly, speculation is that this will be the vehicle Uber’s Elevate air taxi program. This initiative by Uber intends to turn a random parking lot in LA into the busiest airport in the world. This is what the official marketing material from Uber says, I am not making this up, and it’s beyond stupid. You know what, just have Uber buy the Santa Monica airport, close it down, and turn it into an air taxi hub. This is the dumbest and funniest possible future imaginable.
Okay, CES is terrible, but here’s something for you. You can get a free ‘maker license’ of Solidworks. Just go here and enter promo code ‘918MAKER’. This info comes from reddit.
The Impossible Project was founded in 2008 as an initiative to remanufacture Polaroid film and refurbish cameras. The project was a rousing success with many supporters. It is a beacon of hope for anyone who wants to keep obsolete formats alive. Now, another format will live on. MacEffects, a company (or eBay store) in Indiana is remanufacturing color ribbons for Apple ImageWriter II printers. The ImageWriter II was the dot-matrix printer in your elementary school’s computer lab if you’re in the Oregon Trail generation, and yes, it could print color pictures. It could print very high-quality color pictures. The problem is getting color ribbons, and now you can get new ones. We’re very interested in seeing the art that can be made with a color ribbon in an ImageWriter, so if you have a portfolio, send it on in. If you have an ImageWriter, try to print something. It’s a serial printer, not a parallel printer.
Hackaday Links: November 25, 2018
Bad Obsession Motorsport have been stuffing the engine and suspension from a 4WD Celica into an old Mini since forever. It is a wonderful homage to Police Squad and some of the best machining and fabrication you’ll see on YouTube. The latest episode tackled the electrical system and how to drive an alternator in an extremely cramped engine bay. The solution was a strange flex-shaft confabulation, and now the Bad Obsession Motorsport guys have a video on how they attached an alternator to a car where no alternator should go. It’s forty minutes of machining, go watch it.
Last Friday was Black Friday, and that means it’s time to CONSUME CONSUME CONSUME. Tindie’s having a sale right now, so check that out.
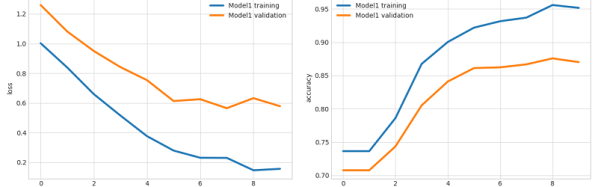
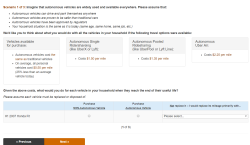
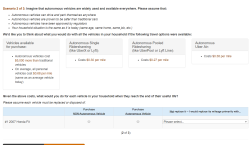
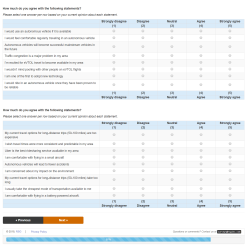
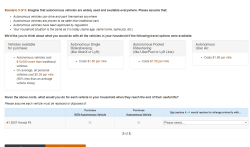
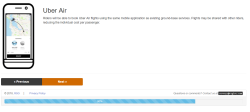
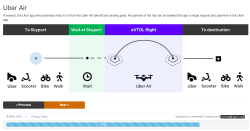
I’m the future of autonomous flight! This week, I got a market research survey in my email from Uber, wanting me to give my thoughts on autonomous ridesharing VTOL aircraft. Uber’s current plan for ridesharing small aircraft involves buying whatever Embraer comes up with (Uber is not developing their own aircraft), not having pilots (this will never get past the FAA), and turning a random parking lot in LA into the busiest airport in the world (by aircraft movements, which again is something that will never get past the FAA). Needless to say, this is criminally dumb, and I’m more than happy to give my thoughts. Below are the relevant screencaps of the survey:
The crux of this survey is basic market research; how much would I pay for a VTOL ride sharing service versus buying a new (autonomous) car versus using an autonomous Uber. You’ve also got a Likert scale thingy asking me if I’m comfortable flying in a battery-powered aircraft. Protip: I highly doubt anyone given this survey has flown in a battery-powered aircraft. Proprotip: the easiest way to screw up the scoring for a Likert scale is to answer ‘1’ for the first question, ‘2’ for the second, etc., and wrap back around to ‘1’ for the sixth question.
Don’t worry, though: I answered all the questions truthfully, but Uber Air will never happen. The FAA won’t let this one fly, and no company will ever carry passengers without a licensed pilot on board.
Fatalities Vs False Positives: The Lessons From The Tesla And Uber Crashes
In one bad week in March, two people were indirectly killed by automated driving systems. A Tesla vehicle drove into a barrier, killing its driver, and an Uber vehicle hit and killed a pedestrian crossing the street. The National Transportation Safety Board’s preliminary reports on both accidents came out recently, and these bring us as close as we’re going to get to a definitive view of what actually happened. What can we learn from these two crashes?
There is one outstanding factor that makes these two crashes look different on the surface: Tesla’s algorithm misidentified a lane split and actively accelerated into the barrier, while the Uber system eventually correctly identified the cyclist crossing the street and probably had time to stop, but it was disabled. You might say that if the Tesla driver died from trusting the system too much, the Uber fatality arose from trusting the system too little.
But you’d be wrong. The forward-facing radar in the Tesla should have prevented the accident by seeing the barrier and slamming on the brakes, but the Tesla algorithm places more weight on the cameras than the radar. Why? For exactly the same reason that the Uber emergency-braking system was turned off: there are “too many” false positives and the result is that far too often the cars brake needlessly under normal driving circumstances.
The crux of the self-driving at the moment is precisely figuring out when to slam on the brakes and when not. Brake too often, and the passengers are annoyed or the car gets rear-ended. Brake too infrequently, and the consequences can be worse. Indeed, this is the central problem of autonomous vehicle safety, and neither Tesla nor Uber have it figured out yet.
Continue reading “Fatalities Vs False Positives: The Lessons From The Tesla And Uber Crashes”